Let's just say that stealing personal information on the Internet is illegal (and ugly). The sole purpose of our editorial experiment was to show how dangerous public Wi-Fi networks can be. All received information (as well as all "spyware" programs) was deleted from the computer immediately after the experiment ended.
Users are now so careless that it's easy for them to accidentally lose sensitive data. We set out to show how many "holes" there are in public Wi-Fi networks.
And they themselves were afraid of how easy it is to leave a complete dossier on themselves to a stranger, but interested person.
"Use only if you are fully aware of your actions"
We prepared for the experiment thoroughly. We installed several programs at once. They are slightly different in functionality, but they have the same essence-to collect everything that passes through the network to which the computer is connected. Even over Wi-Fi. Even from other people's devices.
None of the programs are labeled as "pirated", "hacker" or illegal-they can be downloaded online without any problems. True, the antivirus immediately tries to remove one as malicious, but it reacts calmly to the other.
Reading the instructions:
"Use this monitoring mode only if you are fully aware of your actions, "one of the spies asks. And adds that its technology is based on the weaknesses of the ARP protocol. Are we aware of our actions? Yes of course!
I go to a cafe in the middle of the Minsk shopping center, taking with me my partner-the "victim" and two laptops. You can immediately see that the cafe has free Wi – Fi, five people are sitting outside with gadgets, and even more inside.
I instruct my partner: he must log in to the Internet via Wi-Fi and behave like a normal user. On his computer, Windows 8 is installed with built-in antivirus and firewall - a standard option, few people bother installing more advanced protection software.

I set up a computer with spyware at a table and try to track what the "victim" is doing on the Internet.

Computers - by list, other people's data - by time
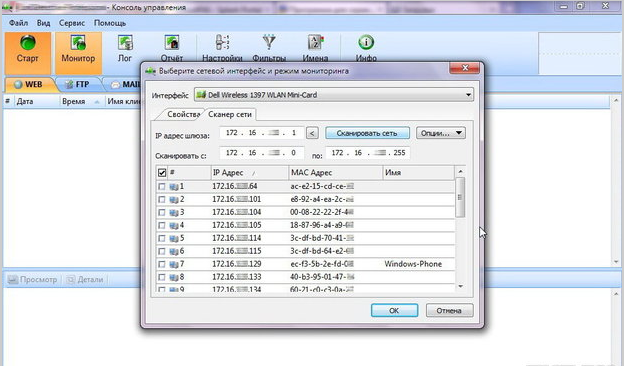
Connecting to Wi-Fi: there is no password, the network name contains the word "free". I start scanning, one of the programs immediately finds 15 network connections. You can see the IP address and MAC address for each of them, and the name of the device manufacturer for some of them: Sony, Samsung, Apple, LG, HTC...
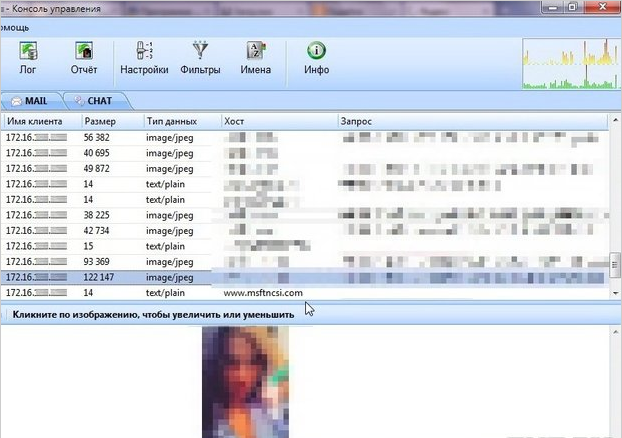
I find my partner's laptop among the devices. I connect to it – data that passes through the network begins to appear on the screen. All information is structured by time, and there is even a built-in intercepted data viewer.
We exchange glances with our partner, who understands that the surveillance was successful, and decides to change the site.
The "victim" is sitting a couple of meters away, and we stare at her photo on the Internet
I keep watching. An online game has clearly started on the partner's laptop: software commands are constantly being sent to the network, and information about the situation on the battlefield is being received. You can see the nicknames of your opponents, their game levels, and much more.
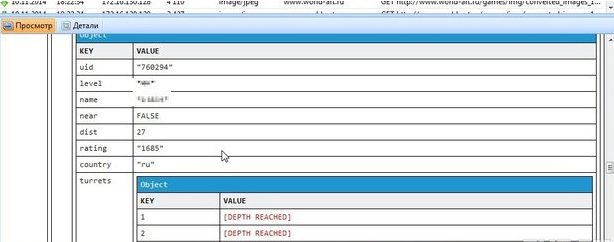
The message "Facebook" arrives. In one of the detailed message specifications, we find that the user ID is visible in each of them. If you paste it in the browser, the account of the person who received the message will open.
We open the page of the partner "Facebook": the page contains the first name, last name and a whole bunch of other information.
My partner is currently replying to the message, and clearly doesn't realize that we're all gawking at the photos on his account. One of the social network applications sends a signal – we can listen to this sound in the player while sitting two meters away.
Beyond: Password and message interception features
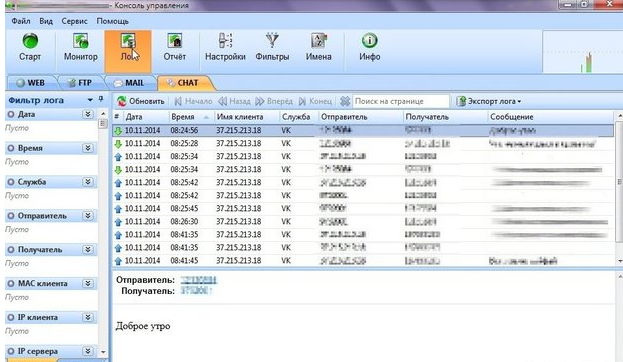
Photos and sounds are not all that can be "given" to an available Wi-Fi network. For example, in one of the programs there is a separate tab to track exactly the correspondence in social networks and messengers. Messages are decrypted and sorted by the time they were sent.
Showing someone else's correspondence is already beyond good and evil. But it works. As an illustration – a part of the text author's dialog caught by the tracking computer from the"victim" device.
Another program stores all cookies and user information, including passwords, separately. Fortunately, it's encrypted, but it immediately suggests installing a utility that will decrypt them. We firmly decide not to do this, although a lot of "good" is gained in a few sessions.

"Intercept attempt detected"
It turns out that almost any information can be lost via Wi-Fi. Although everything is not so bad: similar programs do not work everywhere. For example, in another cafe, the insidious plan was immediately revealed. Instead of the MAC addresses of the neighbors ' computers, the program returned only one address – mine-with a comment that an attempt to intercept traffic was detected.
But this is an isolated case. Many public networks do not provide any protection at all, and sometimes even a password. This means that the traffic of colleagues, friends, or strangers can be intercepted by anyone.
The most reliable way out of this situation is one: do not transmit any important information through public networks. For example, do not send phone numbers and passwords in messages and do not pay with a payment card outside the home.
It is also advisable to be more responsible about protecting your device, otherwise you need to be ready to say goodbye to personal information.
Users are now so careless that it's easy for them to accidentally lose sensitive data. We set out to show how many "holes" there are in public Wi-Fi networks.
And they themselves were afraid of how easy it is to leave a complete dossier on themselves to a stranger, but interested person.
"Use only if you are fully aware of your actions"
We prepared for the experiment thoroughly. We installed several programs at once. They are slightly different in functionality, but they have the same essence-to collect everything that passes through the network to which the computer is connected. Even over Wi-Fi. Even from other people's devices.
None of the programs are labeled as "pirated", "hacker" or illegal-they can be downloaded online without any problems. True, the antivirus immediately tries to remove one as malicious, but it reacts calmly to the other.
Reading the instructions:
"Use this monitoring mode only if you are fully aware of your actions, "one of the spies asks. And adds that its technology is based on the weaknesses of the ARP protocol. Are we aware of our actions? Yes of course!
I go to a cafe in the middle of the Minsk shopping center, taking with me my partner-the "victim" and two laptops. You can immediately see that the cafe has free Wi – Fi, five people are sitting outside with gadgets, and even more inside.
I instruct my partner: he must log in to the Internet via Wi-Fi and behave like a normal user. On his computer, Windows 8 is installed with built-in antivirus and firewall - a standard option, few people bother installing more advanced protection software.

I set up a computer with spyware at a table and try to track what the "victim" is doing on the Internet.

Computers - by list, other people's data - by time
Connecting to Wi-Fi: there is no password, the network name contains the word "free". I start scanning, one of the programs immediately finds 15 network connections. You can see the IP address and MAC address for each of them, and the name of the device manufacturer for some of them: Sony, Samsung, Apple, LG, HTC...

I find my partner's laptop among the devices. I connect to it – data that passes through the network begins to appear on the screen. All information is structured by time, and there is even a built-in intercepted data viewer.

We exchange glances with our partner, who understands that the surveillance was successful, and decides to change the site.
The "victim" is sitting a couple of meters away, and we stare at her photo on the Internet
I keep watching. An online game has clearly started on the partner's laptop: software commands are constantly being sent to the network, and information about the situation on the battlefield is being received. You can see the nicknames of your opponents, their game levels, and much more.

The message "Facebook" arrives. In one of the detailed message specifications, we find that the user ID is visible in each of them. If you paste it in the browser, the account of the person who received the message will open.
We open the page of the partner "Facebook": the page contains the first name, last name and a whole bunch of other information.
My partner is currently replying to the message, and clearly doesn't realize that we're all gawking at the photos on his account. One of the social network applications sends a signal – we can listen to this sound in the player while sitting two meters away.
Beyond: Password and message interception features
Photos and sounds are not all that can be "given" to an available Wi-Fi network. For example, in one of the programs there is a separate tab to track exactly the correspondence in social networks and messengers. Messages are decrypted and sorted by the time they were sent.
Showing someone else's correspondence is already beyond good and evil. But it works. As an illustration – a part of the text author's dialog caught by the tracking computer from the"victim" device.

Another program stores all cookies and user information, including passwords, separately. Fortunately, it's encrypted, but it immediately suggests installing a utility that will decrypt them. We firmly decide not to do this, although a lot of "good" is gained in a few sessions.

"Intercept attempt detected"
It turns out that almost any information can be lost via Wi-Fi. Although everything is not so bad: similar programs do not work everywhere. For example, in another cafe, the insidious plan was immediately revealed. Instead of the MAC addresses of the neighbors ' computers, the program returned only one address – mine-with a comment that an attempt to intercept traffic was detected.
But this is an isolated case. Many public networks do not provide any protection at all, and sometimes even a password. This means that the traffic of colleagues, friends, or strangers can be intercepted by anyone.
The most reliable way out of this situation is one: do not transmit any important information through public networks. For example, do not send phone numbers and passwords in messages and do not pay with a payment card outside the home.
It is also advisable to be more responsible about protecting your device, otherwise you need to be ready to say goodbye to personal information.







