- Joined
- Nov 26, 2020
- Messages
- 714
Vulnerabilities in popular smartphone keyboards allow you to see what the user is typing.
Citizen Lab identified vulnerabilities in popular keyboard applications that can be used to register keystrokes of Chinese users around the world. Security issues are present in almost all apps, including those that are pre-installed on Android devices in China.
The researchers analyzed versions of keyboard apps for Android, iOS, and Windows from Tencent, Baidu, iFlytek, Sogou, Samsung, Huawei, Xiaomi, OPPO, Vivo, and Honor. The first four-Tencent, Baidu, iFlytek, and Sogou-are separate keyboard software developers, while the rest — Samsung, Huawei, Xiaomi, OPPO, Vivo, and Honor — are mobile device manufacturers who either developed their own keyboards or pre-installed one or more of the other three developers ' apps on their devices.
The keyboard apps of Baidu, Tencent, iFlytek, and Sogou are used to make typing Chinese characters easier, but many of them don't protect the data being transmitted properly. Particularly worrisome is the lack of TLS (Transport Layer Security), an encryption standard that could prevent data interception.
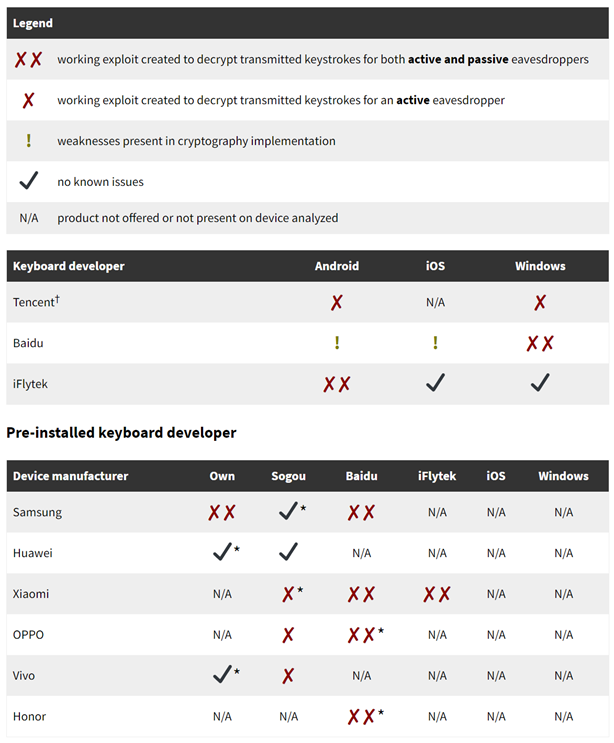
Summary table of vulnerabilities found in popular keyboard apps and keyboards pre-installed on popular smartphones
The discovery of vulnerabilities became possible after researchers discovered that the Sogou application sent data without using TLS, which allowed third parties to intercept and decrypt the entered information. Even though Sogou fixed the issue after publishing, some pre-installed keyboards are still not updated.
The ease of exploiting the discovered vulnerabilities and possible consequences, including the leakage of passwords and confidential data, highlight the severity of the problem. Experts say that exploiting the shortcomings does not require significant computing power, and basic knowledge is enough to intercept data in public Wi-Fi networks.
The problem is compounded by the fact that many of the keyboard applications were developed in the 2000s, before the widespread adoption of TLS in software development. After the security issues became known, most of the vulnerabilities were fixed, but some companies still did not respond to reports of problems, and vulnerabilities still exist.
Additional research efforts, including changing the email headers and text to Chinese, led iFlytek to respond to the emails and fix the problems. But data security issues continue to be relevant for millions of users, emphasizing the need for closer cooperation and information exchange between researchers from different countries.
Citizen Lab identified vulnerabilities in popular keyboard applications that can be used to register keystrokes of Chinese users around the world. Security issues are present in almost all apps, including those that are pre-installed on Android devices in China.
The researchers analyzed versions of keyboard apps for Android, iOS, and Windows from Tencent, Baidu, iFlytek, Sogou, Samsung, Huawei, Xiaomi, OPPO, Vivo, and Honor. The first four-Tencent, Baidu, iFlytek, and Sogou-are separate keyboard software developers, while the rest — Samsung, Huawei, Xiaomi, OPPO, Vivo, and Honor — are mobile device manufacturers who either developed their own keyboards or pre-installed one or more of the other three developers ' apps on their devices.
The keyboard apps of Baidu, Tencent, iFlytek, and Sogou are used to make typing Chinese characters easier, but many of them don't protect the data being transmitted properly. Particularly worrisome is the lack of TLS (Transport Layer Security), an encryption standard that could prevent data interception.

Summary table of vulnerabilities found in popular keyboard apps and keyboards pre-installed on popular smartphones
The discovery of vulnerabilities became possible after researchers discovered that the Sogou application sent data without using TLS, which allowed third parties to intercept and decrypt the entered information. Even though Sogou fixed the issue after publishing, some pre-installed keyboards are still not updated.
The ease of exploiting the discovered vulnerabilities and possible consequences, including the leakage of passwords and confidential data, highlight the severity of the problem. Experts say that exploiting the shortcomings does not require significant computing power, and basic knowledge is enough to intercept data in public Wi-Fi networks.
The problem is compounded by the fact that many of the keyboard applications were developed in the 2000s, before the widespread adoption of TLS in software development. After the security issues became known, most of the vulnerabilities were fixed, but some companies still did not respond to reports of problems, and vulnerabilities still exist.
Additional research efforts, including changing the email headers and text to Chinese, led iFlytek to respond to the emails and fix the problems. But data security issues continue to be relevant for millions of users, emphasizing the need for closer cooperation and information exchange between researchers from different countries.


















