- Joined
- Nov 26, 2020
- Messages
- 716

Mobile phone viruses of the future can be as debilitating as computer viruses.
The first known cell phone virus appeared in 2004 and hasn't made much headway. Cabir only infected a small number of Bluetooth-enabled phones and took no malicious action - the malware team created Cabir to prove it was possible. Their next step was to send it to antivirus researchers, who began the process of developing a solution to a problem that promises to get worse.
Cell phone viruses are on the cusp of their effectiveness. Currently, they cannot spread very far and do not do much harm, but in the future, cell phone bugs may appear as debilitating as computer viruses. In this article, we'll talk about how cell phone viruses spread, what they can do, and how you can protect your phone from current and future threats.
Mobile phone virus basics
A virus for mobile phones is basically the same as a computer virus - an unwanted executable file that "infects" a device and then copies itself to other devices. But while a computer virus or worm spreads through email attachments and Internet downloads, a mobile phone virus or worm spreads through Internet downloads, MMS (Multimedia Messaging Service) attachments, and Bluetooth transmission. The most common type of cell phone infection now occurs when a cell phone downloads an infected file from a PC or the Internet, but the number of viruses transmitted from phone to phone is on the rise.
Modern viruses are transmitted from phone to phone, almost always infect phones running under the control of the operating system the Symbian . The large number of proprietary operating systems in the world of cell phones is one of the obstacles to mass infection. Mobile phone virus makers do not have a market share at the Windows level, so any virus will only affect a small percentage of phones.
Infected files usually appear under the guiselike apps like games, security patches, added functionality, and of course, pornography and free stuff. Infected text messages sometimes steal the subject line from a message you received from a friend, which of course increases the likelihood that you will open it, but opening the message is not enough to get infected. You must open the attachment to the message and agree to the installation of the program, which is another obstacle to mass infection: to date, not a single automatic installation of a virus between phones has been registered. Installation barriers and distribution methods limit the damage that the current generation of mobile phone viruses can do.
What's with Paris Hilton's phone
Remember when someone got on Paris Hilton's stellar contact list? This was not the result of a virus and no one was hacking into Hilton's phone. Mobile phone servers store certain types of information, such as contact lists (in case the user's phone is locked) and recent calls (for billing purposes). An enterprising hacker infiltrated T-Mobile's servers and stole information from there.
How they spread
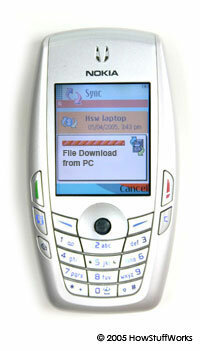
Cell phones can catch viruses while downloading an infected file.
Phones that can only make and receive calls are not at risk. Only smartphones with Bluetooth connectivity and data transfer capability can get the cell phone virus. These viruses spread mainly in three ways:
- Загрузки из Интернета. Вирус распространяется так же, как и традиционный компьютерный вирус. Пользователь загружает зараженный файл в телефон через компьютер или собственное Интернет-соединение телефона. Это может включать в себя загрузку файлов для совместного использования, приложения, доступные с дополнительных сайтов (например, рингтоны или игры), и ложные исправления безопасности, размещенные на веб-сайте Symbian.
- Bluetooth wireless connection . The virus spreads between phones via a Bluetooth connection. The user receives the virus via Bluetooth when the phone is in discoverable mode, meaning it can be seen on other Bluetooth-enabled phones. In this case, the virus spreads like an airborne disease. According to TechnologyReview.com, cell phone virus researchers at the US F-Secure lab are now conducting their research in a bomb shelter, so their research topics are not being extended to all nearby Bluetooth-enabled phones.
- Multimedia messaging service . The virus is an attachment to an MMS text message. As with computer viruses that arrive as email attachments, the user must open the attachment and then install it in order for the virus to infect the phone. Typically, a virus spreading via MMS enters the phone's contact list and is sent to every phone number stored in it.
The Commwarrior virus arrived locally in January 2005 and is the first cell phone virus to spread efficiently through a whole company via Bluetooth (see ComputerWorld.com: the virus spreads through the phone of a Scandinavian company). It is copied both via Bluetooth and MMS. Once you get and install the virus, it will immediately start looking for other Bluetooth phones in the vicinity to infect them. At the same time, the virus sends infected MMS messages to every phone number in your address list. Commwarrior is probably one of the most effective viruses out there today because it uses two methods to replicate itself.
So what does a virus like this do when it infects your phone?
Damage done
The first known virus for mobile phones, Cabir, is completely harmless. All he does is sit on the phone and try to spread. However, other mobile phone viruses are not as harmless.
The virus can access and / or delete all contact information and calendar entries on your phone. It can send an infected MMS message to every number in your phone book, and sending MMS messages usually costs money, so you actually pay to send the virus to all your friends, family and business partners. In the worst case, it can uninstall or block certain phone apps, or completely disable it, so that it is useless. Some of the registered viruses and their vital statistics are listed below.
As you can see from the descriptions above, mobile phone viruses have become much more dangerous since the Cabir worm got into the hands of researchers in 2004. On the other hand, there are several steps you can take to protect your phone.
Viruses for
Cabir mobile phones
First reported: June 2004
Attacks: Symbian Series 60 phones
Spread through: Bluetooth
Harm: none
Additional information (including treatment): http://www.f-secure.com/v-descs/cabir. shtml
Skulls
First message: November 2004
Attacks: various Symbian phones
Distributed via: Internet download
Harm: disables all phone functions except for sending / receiving calls
Additional information (including treatment): http://www.f-secure.com/v-descs/skulls.shtml
Commwarrior
First message: January 2005
Attacks: Symbian phones Series 60
Distributed via: Bluetooth and MMS.
Harm: Sends expensive MMS to everyone in the phone book (when replicating MMS)
Additional information (including treatment): http://www.f-secure.com/v-descs/commwarrior.shtml
Locknut B
First message: March 2005
Attacks : Symbian Series 60 phones
Distributed via: Internet download (disguised as a patch for Symbian Series 60 phones)
Harm: the system ROM crashes; disables all phone functions; inserts other (inactive) malware into the phone
Additional information (including treatment): http://www.f-secure.com/v-descs/locknut_b.shtml
Fontal A
First message: April 2005
Attacks: Symbian Series 60 phones
Distributed through: Internet download
Harm: blocks the phone in startup mode; turns off the phone completely
More information (including treatment): http://www.f-secure.com/v-descs/fontal_a.shtml
Protecting your phone
The best way to protect yourself from cell phone viruses is the same way to protect yourself from computer viruses: never open anything unless you know what it is, have not asked for it, or have any suspicion that it is not. what do you need. claims to be. However, even the most cautious person can end up with an infected phone. Here are some steps you can take to reduce your chances of getting a virus:
- Disable Bluetooth discovery mode. Set your phone to "hidden" so that other phones cannot detect it and send a virus. You can do this from the Bluetooth options screen.
- Check the security updates for file names to watch out for. This is unsafe - Commwarrior generates random names for the infected files it sends, so users cannot be warned not to open certain filenames - but many viruses can be easily identified by the filenames they carry. Security sites with detailed information on viruses include: F-Secure , McAfee, and Symantec .
- Some of these sites will send you email updates with information about new viruses as they are posted.
- Install any security software on your phone. Many companies develop security software for cell phones, some are free to download, some are purchased by users, and some are for cell phone service providers. The software can simply detect and then remove the virus once it has been received and installed, or it can protect your phone from being infected with certain viruses. Symbian has developed an anti-virus version of its operating system that only accepts secure files via the phone's Bluetooth connection.
While some in the cell phone industry believe the potential problem is exaggerated, most experts agree that cell phone viruses are on the brink of destructiveness. Installing a "security patch" that ultimately turns your phone into a useless piece of plastic is definitely a concern, but it can still get worse. Opportunities for the future include viruses that cause errors in phones so that someone can see every number you call and listen to your conversations, and viruses that steal financial information, which could be a major problem if smartphones eventually become be used as payment devices (see Bankrate.com: Pay by mobile phone on the go). Ultimately, more connections means more exposure to viruses and faster spread of infection. As smartphones become more widespread and sophisticated, so will viruses targeting them.













