- Joined
- Dec 3, 2020
- Messages
- 1,722
In this article we will be looking at the different kinds of malware and what they do. When performing static or dynamic malware analysis it is crucial to have a good understanding of the different malware types available so you are able to recognize them and focus your investigation. During static malware analysis the imported DLL’s and functions often tell us a lot about the malware’s intentions and behaviour. For example when malware imports networking functions together with functions to edit the Windows registry and compression functions, we could be dealing with spyware, a downloader malware or a Trojan which executes itself or other malware at start up. In the simplest case of statically imported DLL’s you can use an application like Dependency Walker to find out which functions are used in malware. Further inspection of the DLL’s, functions, PE headers and resources should narrow the possible kinds of malware a lot. Let’s continue to look at the different kinds of malware available and what they exactly do.
Adware
Adware as malware is malicious software which presents unwanted advertising to the user. This kind of malware often uses pop-up windows which cannot be closed by the user. Adware is often included with free software and browser toolbars. Malware which is also collecting user data, activity and other information for targeted advertising is called spyware.
Backdoor
A backdoor is a piece of malicious code which allows an attacker to connect to the infected target and take control of the target machine. In most cases there is no authentication required to log in the remote machine other than authentication methods required by the malware. A backdoor is often generated by a Trojan which goes unnoticed if the host has no effective detection mechanisms. Backdoors can use a lot of methods to communicate home. Also port 80 is commonly used by malware over the HTTP protocol because this port is open on most machines connected to the internet. We will discuss 2 kinds of backdoors; the reverse shell and the Remote Access/Administration Tool (RAT).
Reverse Shell
A reverse shell is a connection initiated from the infected host to the attacker and provides the attacker with a shell access to the host. The reverse shell is often created by a Trojan and functions as a backdoor on the infected host. After the reverse shell has been set up the attacker is able to execute commands as if they were executed locally. There are a couple ways for malware developers to set up a reverse shell. Commonly used methods for reverse shells are Netcat and Windows cmd.exe packaged inside malware. A simple method used by malware using the Windows CMD to set up a reverse shell is to create a socket to establish a connection to the attacker and than tying it to the standard streams (standard input, output and error) for cmd.exe. The cmd.exe is than run with suppressed window to hide it from the victim’s view and can than be used to execute commands on the infected host.
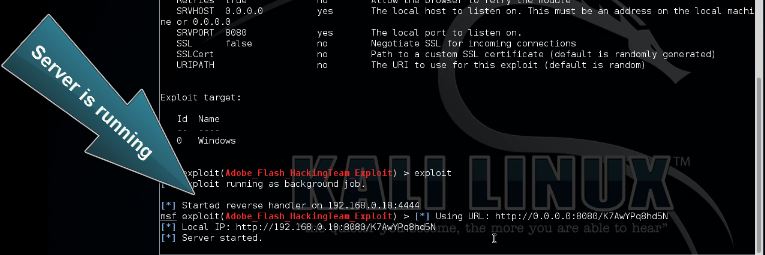
RAT – Remote Access Trojan
A Remote Access Trojan (RAT), or sometimes called a Remote Administration Tool or Remote Access Tool, is software which allows an attacker to take control of the infected host by the use of a backdoor. We’ll call it a Remote Access Trojan in this article to emphasize the maliciousness of this kind of RAT. We are talking about the malicious RAT’s and not the ones which are used by system administrators or software vendors for remote support and troubleshooting. Remote Access Trojans are often included with free software and send as attachment by e-mail.
Botnet
A botnet is a network of remote controlled private computers with backdoors which are being controlled by a command and control server. All infected hosts in the botnet are controlled as a group and receive the same instructions from the server which is controlled by the attacker. Botnets are often used to send spam, to perform distributed denial-of-service (DDoS) attacks or malware distribution.
Browser Hijacker
A browser hijacker is a piece of malicious code developed to control your browser settings like the homepage for example, or the standard search provider. Browser hijackers are often included with free software and browser toolbars and may also contain adware and spyware. Some browser hijackers also change your browser’s proxy settings which compromises your online privacy and safety.
Downloader Malware
Downloader Malware is malicious software which downloads other malicious software. Attackers often infect a machine with downloader malware when they have gained first access to the system. The downloader malware than infects the target machine silently with other malware.
Information Stealing Malware
Information stealing malware is a collection of malware types which are developed to steal information like credit card numbers, bank account details, account details and other personal information. The collected information is usually send to the attacker who often uses it to gain access to your personal account or to put it up for sale on the deep web. Information stealing malware often comes in the form as keyloggers, password (hash) grabbers and sniffers. The stolen information is often send to a command and control server for further processing.
Keyloggers
Keylogger malware is a malicious piece of software (or hardware) which records your keystrokes in order to retrieve passwords, conversations and other personal details. The recorded keystrokes are than send to the attacker. A keylogger is a very effective way for attackers to steal passwords because there is no need to crack hashes, decrypt information or to sniff secured connections for passwords.
Launcher malware
A launcher is a piece of malicious software which is used to launch other malware. This piece of malicious software is often combined with downloader malware. The launcher malware often uses stealthy and unconventional methods to launch other malicious code to avoid detection.
Ransomware
Technically speaking all malware which prevents a user from accessing the computer or files and demanding money in exchange for access is called ransomware. Ransomware often encrypts your hard drive or files and demands money in exchange for the decryption key. This kind of ransomware is also called a crypto locker. After infection the ransomware presents the user some payments methods which can be used to unlock the computer or decrypt the files. If the ransomware or crypto locker will actually unlock your hard drive or files, the decryption keys and payment are often controlled by a command and control server.
Ransomware has become increasingly popular over time because it is highly profitable for malware developers. Especially ransomware in combination with anonymous payments methods like bitcoin are making this kind of malware very profitable and lowering the risks of getting caught. Popular ransomware malware is: Cryptolocker, Cryptowall and Tox ransomware which is known as the first ransomware as a service available for everybody through the TOR network.
Rootkit
A rootkit is malicious software designed to conceal the existence of other malware. The concealed malware is often a backdoor to provide full access to the attacker or information stealing malware. Rootkits may be hard to detect and remove based on where the rootkit resides. Rootkits on firmware level for example may require hardware replacement and rootkits on kernel level may require a new installation of the operating system.
Bootkit
Another dangerous and almost impossible to detect rootkit is the bootkit. The bootkit is a rootkit hidden in the boot sector that infects the Master Boot Record. This kind of rootkit is able to bypass drive encryption for example because the Master Boot Record (MBR) is not encrypted. The MBR contains the decryption software to decrypt the drive. A bootloader is a piece of codes which runs before the operating system does.
Scareware
Scareware is malicious software which forces the victim into purchasing something by frightening him or her. You might call it blackmailing malware too since it often includes embarrassing viruses or files. The most common scareware malware looks like a virus scanner which has detected some viruses which will be removed after the victim has purchased the virus scanner. In reality only the scareware will be removed (hopefully). Scareware often uses scare tactics which will embarrass the victim to avoid that the victim escalates the problem to a system administrator at work or call in professional help for virus removal for example. Because of these tactics a lot of victims will pay for the software to have the virus or other embarrassing materials removed silently. Scareware or blackmailing malware is just like ransomware, very profitable for malware developers.
Spam Sending Malware
Spam Sending Malware is malicious software which uses the infected machine to send spam. The spam sending malware might be part of a botnet controlled by a command and control server functioning as a distributed spam sending network. Because of the distributed approach there is not a single point of failure, if ¼ of the infected machines are cleaned the other ¾ will keep sending spam mails. Big botnets can send billions of spam messages per week and very often new malware is spread together with the spam messages. Spam sending malware can get you into trouble because ISP’s cut off your internet connection or you e-mail address can be blacklisted so be sure to remove this kind of malware as soon as possible. This type of malware is profitable for malware developers because they can sell the spam sending services.
Trojan
A Trojan or a Trojan horse as malware is a malicious program functioning as a backdoor. Just like the ancient Greek story of the wooden horse with Greek troops inside which was used to invade the city of Troy, a Trojan in computing tends to appear like a regular application, media or any other file but containing a malicious payload. Trojans are often spread through social engineering where the victim is fooled into executing the file or application with the Trojan. Most Trojans contain backdoors which can be used by the attacker to steal information, spread other malware or use the infected machine’s resources in a botnet. Literally anything is possible when infected with a Trojan which was installed or run with elevated privileges. Trojans in computing have been around for a long time, a few old and popular Trojans are: Netbus, SubSeven or Sub7 and Back Orifice or BO in short.
Trojans are often packed in files like this one containing names which might make you curious for what’s inside…
Virus
A virus is a malicious program which replicates itself into other applications, files or even the boot sector. A virus then can do anything it is programmed to like stealing information, log keystrokes or even render a computer useless. The defining characteristic of a virus lies in the self-replication and insertion of malicious code into other programs without user consent. Just like most other malware a virus is designed for seeking profit.
Worm
A worm is a piece of malware that replicates itself in order to spread and infect other systems. Computer worms use the network, links, P2P networks, e-mail and exploit vulnerabilities to spread themselves. Often more than one wat is used to spread the worm. The difference with a virus is that a virus inserts code into other programs where a worm does not and replicates only itself. Worms do not necessarily contain a payload but most worms do. Worms can also be designed to only spread without a payload.
Adware
Adware as malware is malicious software which presents unwanted advertising to the user. This kind of malware often uses pop-up windows which cannot be closed by the user. Adware is often included with free software and browser toolbars. Malware which is also collecting user data, activity and other information for targeted advertising is called spyware.
Backdoor
A backdoor is a piece of malicious code which allows an attacker to connect to the infected target and take control of the target machine. In most cases there is no authentication required to log in the remote machine other than authentication methods required by the malware. A backdoor is often generated by a Trojan which goes unnoticed if the host has no effective detection mechanisms. Backdoors can use a lot of methods to communicate home. Also port 80 is commonly used by malware over the HTTP protocol because this port is open on most machines connected to the internet. We will discuss 2 kinds of backdoors; the reverse shell and the Remote Access/Administration Tool (RAT).
Reverse Shell
A reverse shell is a connection initiated from the infected host to the attacker and provides the attacker with a shell access to the host. The reverse shell is often created by a Trojan and functions as a backdoor on the infected host. After the reverse shell has been set up the attacker is able to execute commands as if they were executed locally. There are a couple ways for malware developers to set up a reverse shell. Commonly used methods for reverse shells are Netcat and Windows cmd.exe packaged inside malware. A simple method used by malware using the Windows CMD to set up a reverse shell is to create a socket to establish a connection to the attacker and than tying it to the standard streams (standard input, output and error) for cmd.exe. The cmd.exe is than run with suppressed window to hide it from the victim’s view and can than be used to execute commands on the infected host.

RAT – Remote Access Trojan
A Remote Access Trojan (RAT), or sometimes called a Remote Administration Tool or Remote Access Tool, is software which allows an attacker to take control of the infected host by the use of a backdoor. We’ll call it a Remote Access Trojan in this article to emphasize the maliciousness of this kind of RAT. We are talking about the malicious RAT’s and not the ones which are used by system administrators or software vendors for remote support and troubleshooting. Remote Access Trojans are often included with free software and send as attachment by e-mail.
Botnet
A botnet is a network of remote controlled private computers with backdoors which are being controlled by a command and control server. All infected hosts in the botnet are controlled as a group and receive the same instructions from the server which is controlled by the attacker. Botnets are often used to send spam, to perform distributed denial-of-service (DDoS) attacks or malware distribution.
Browser Hijacker
A browser hijacker is a piece of malicious code developed to control your browser settings like the homepage for example, or the standard search provider. Browser hijackers are often included with free software and browser toolbars and may also contain adware and spyware. Some browser hijackers also change your browser’s proxy settings which compromises your online privacy and safety.
Downloader Malware
Downloader Malware is malicious software which downloads other malicious software. Attackers often infect a machine with downloader malware when they have gained first access to the system. The downloader malware than infects the target machine silently with other malware.
Information Stealing Malware
Information stealing malware is a collection of malware types which are developed to steal information like credit card numbers, bank account details, account details and other personal information. The collected information is usually send to the attacker who often uses it to gain access to your personal account or to put it up for sale on the deep web. Information stealing malware often comes in the form as keyloggers, password (hash) grabbers and sniffers. The stolen information is often send to a command and control server for further processing.
Keyloggers
Keylogger malware is a malicious piece of software (or hardware) which records your keystrokes in order to retrieve passwords, conversations and other personal details. The recorded keystrokes are than send to the attacker. A keylogger is a very effective way for attackers to steal passwords because there is no need to crack hashes, decrypt information or to sniff secured connections for passwords.
Launcher malware
A launcher is a piece of malicious software which is used to launch other malware. This piece of malicious software is often combined with downloader malware. The launcher malware often uses stealthy and unconventional methods to launch other malicious code to avoid detection.
Ransomware
Technically speaking all malware which prevents a user from accessing the computer or files and demanding money in exchange for access is called ransomware. Ransomware often encrypts your hard drive or files and demands money in exchange for the decryption key. This kind of ransomware is also called a crypto locker. After infection the ransomware presents the user some payments methods which can be used to unlock the computer or decrypt the files. If the ransomware or crypto locker will actually unlock your hard drive or files, the decryption keys and payment are often controlled by a command and control server.
Ransomware has become increasingly popular over time because it is highly profitable for malware developers. Especially ransomware in combination with anonymous payments methods like bitcoin are making this kind of malware very profitable and lowering the risks of getting caught. Popular ransomware malware is: Cryptolocker, Cryptowall and Tox ransomware which is known as the first ransomware as a service available for everybody through the TOR network.
Rootkit
A rootkit is malicious software designed to conceal the existence of other malware. The concealed malware is often a backdoor to provide full access to the attacker or information stealing malware. Rootkits may be hard to detect and remove based on where the rootkit resides. Rootkits on firmware level for example may require hardware replacement and rootkits on kernel level may require a new installation of the operating system.
Bootkit
Another dangerous and almost impossible to detect rootkit is the bootkit. The bootkit is a rootkit hidden in the boot sector that infects the Master Boot Record. This kind of rootkit is able to bypass drive encryption for example because the Master Boot Record (MBR) is not encrypted. The MBR contains the decryption software to decrypt the drive. A bootloader is a piece of codes which runs before the operating system does.
Scareware
Scareware is malicious software which forces the victim into purchasing something by frightening him or her. You might call it blackmailing malware too since it often includes embarrassing viruses or files. The most common scareware malware looks like a virus scanner which has detected some viruses which will be removed after the victim has purchased the virus scanner. In reality only the scareware will be removed (hopefully). Scareware often uses scare tactics which will embarrass the victim to avoid that the victim escalates the problem to a system administrator at work or call in professional help for virus removal for example. Because of these tactics a lot of victims will pay for the software to have the virus or other embarrassing materials removed silently. Scareware or blackmailing malware is just like ransomware, very profitable for malware developers.
Spam Sending Malware
Spam Sending Malware is malicious software which uses the infected machine to send spam. The spam sending malware might be part of a botnet controlled by a command and control server functioning as a distributed spam sending network. Because of the distributed approach there is not a single point of failure, if ¼ of the infected machines are cleaned the other ¾ will keep sending spam mails. Big botnets can send billions of spam messages per week and very often new malware is spread together with the spam messages. Spam sending malware can get you into trouble because ISP’s cut off your internet connection or you e-mail address can be blacklisted so be sure to remove this kind of malware as soon as possible. This type of malware is profitable for malware developers because they can sell the spam sending services.
Trojan
A Trojan or a Trojan horse as malware is a malicious program functioning as a backdoor. Just like the ancient Greek story of the wooden horse with Greek troops inside which was used to invade the city of Troy, a Trojan in computing tends to appear like a regular application, media or any other file but containing a malicious payload. Trojans are often spread through social engineering where the victim is fooled into executing the file or application with the Trojan. Most Trojans contain backdoors which can be used by the attacker to steal information, spread other malware or use the infected machine’s resources in a botnet. Literally anything is possible when infected with a Trojan which was installed or run with elevated privileges. Trojans in computing have been around for a long time, a few old and popular Trojans are: Netbus, SubSeven or Sub7 and Back Orifice or BO in short.

Trojans are often packed in files like this one containing names which might make you curious for what’s inside…
Virus
A virus is a malicious program which replicates itself into other applications, files or even the boot sector. A virus then can do anything it is programmed to like stealing information, log keystrokes or even render a computer useless. The defining characteristic of a virus lies in the self-replication and insertion of malicious code into other programs without user consent. Just like most other malware a virus is designed for seeking profit.
Worm
A worm is a piece of malware that replicates itself in order to spread and infect other systems. Computer worms use the network, links, P2P networks, e-mail and exploit vulnerabilities to spread themselves. Often more than one wat is used to spread the worm. The difference with a virus is that a virus inserts code into other programs where a worm does not and replicates only itself. Worms do not necessarily contain a payload but most worms do. Worms can also be designed to only spread without a payload.













