- Joined
- Dec 3, 2020
- Messages
- 2,400
And again, social engineering is in use, this time intruders are fooling support agents.
Hacker groups aimed at companies involved in the development of online games using an unprecedented backdoor, which researchers called « IceBreaker » ( translated: « icebreaker » ).
Security Joes incident response experts believe that IceBreaker backdoor uses « very specific social engineering technology ». The method is based on the deception of support agents. An attacker pretends to be a user who is faced with a problem and sends a malicious screenshot to an employee in a chat. There is nothing left for Tom to download and open the file, because you need to help the user. That is how the support agent infects his computer with a virus.
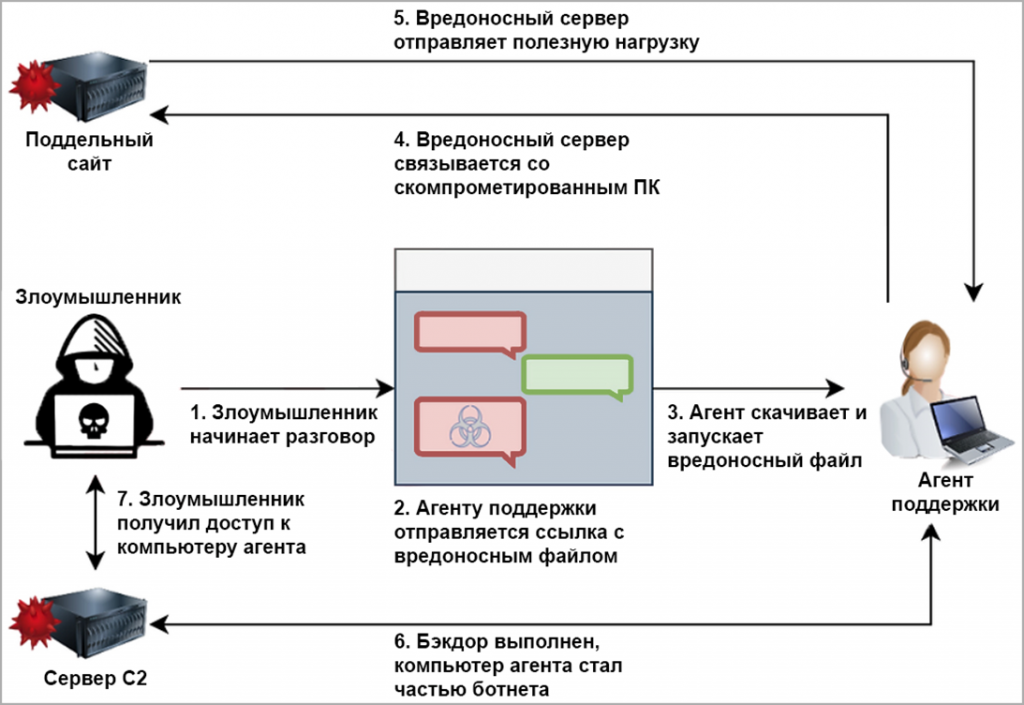
The name of the group behind these attacks remains unknown. However, judging by Security Joes, this group has been using this approach since at least September 2022. At the same time, the only public evidence of using IceBreaker is a post on Twitter from MalwareHunterTeam in October.
A malicious image is usually posted on a fake website that impersonates one of the popular hosting. Although researchers also saw that malicious screenshots were stored in the regular Dropbox repository.
The « image » itself is actually a malicious file with the extension « .lnk ». In fact, this is a regular Windows shortcut, the parameters of which spells out malicious code.
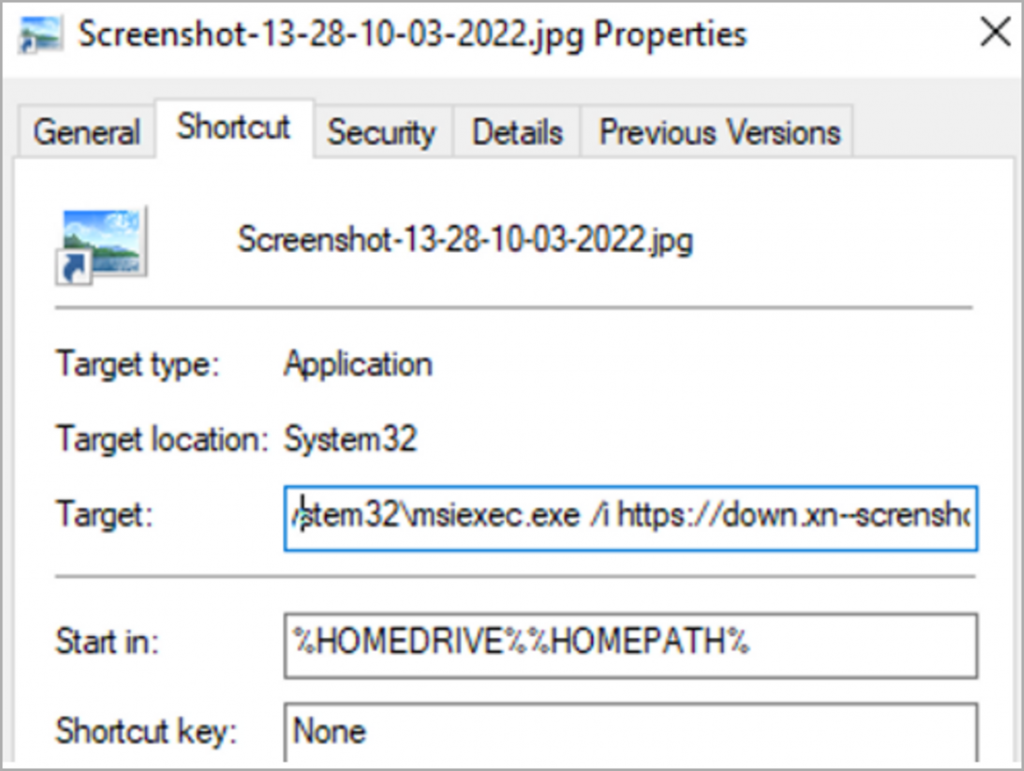
As can be seen in the image above, the label icon has been changed to make it look harmless. The label contains a command for downloading payloads in the « .msi » format from the server of the attacker, its hidden installation and launch without a user interface.
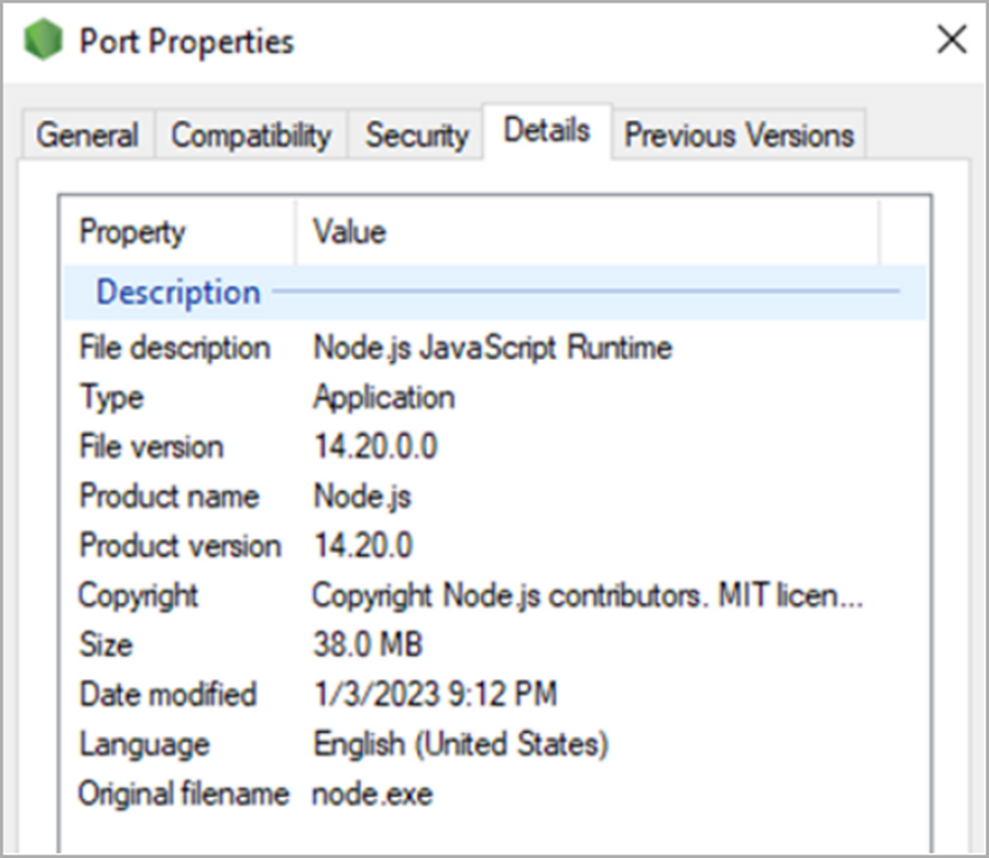
Further along the path « AppData \ Local \ Temp » the malicious application « Port.exe », a 64-bit executable file on C + + is extracted.
After a thorough analysis, Security Joes found out that the sample is a completely new backdoor written in Node.js. It provides the following opportunities for intruders:
Not much is known about IceBreaker, but Security Joes decided to publish this report and share all detected compromising indicators ( IoC ), to help antivirus companies learn how to timely identify and eliminate the threat.
Hacker groups aimed at companies involved in the development of online games using an unprecedented backdoor, which researchers called « IceBreaker » ( translated: « icebreaker » ).
Security Joes incident response experts believe that IceBreaker backdoor uses « very specific social engineering technology ». The method is based on the deception of support agents. An attacker pretends to be a user who is faced with a problem and sends a malicious screenshot to an employee in a chat. There is nothing left for Tom to download and open the file, because you need to help the user. That is how the support agent infects his computer with a virus.

| IceBreaker distribution and activation scheme ( Security Joes ) |
A malicious image is usually posted on a fake website that impersonates one of the popular hosting. Although researchers also saw that malicious screenshots were stored in the regular Dropbox repository.
The « image » itself is actually a malicious file with the extension « .lnk ». In fact, this is a regular Windows shortcut, the parameters of which spells out malicious code.

| Bright disguised as « .jpg » |
Further along the path « AppData \ Local \ Temp » the malicious application « Port.exe », a 64-bit executable file on C + + is extracted.

| Port.exe file properties |
- tuning the backdoor using plugins that expand its built-in functions;
- prescribing a backdoor to Windows autorun;
- discovery of Windows processes;
- theft of passwords and cookies from a local repository, in particular from Google Chrome;
- inclusion of the Socks5 reverse proxy server;
- uploading files to a remote server through web sockets;
- launch of VBS user scripts;
- creation of screenshots;
- creating sessions of the remote shell.
Not much is known about IceBreaker, but Security Joes decided to publish this report and share all detected compromising indicators ( IoC ), to help antivirus companies learn how to timely identify and eliminate the threat.















