- Joined
- Nov 26, 2020
- Messages
- 716
Deanon can cause great damage to a person.
Doxing is the deliberate search and disclosure of information on the Internet about a particular person.
Once upon a time, deanon was already a method of attack in its own right. Gradually, they began to disclose data on the network for the purpose of blackmail, harassment or fraud. Doxing is also often done out of revenge: for example, to former business partners or spouses.
There are many stories on the Internet where a person was bullied by posting information about him in public in social networks, image boards and Telegram channels. And with the development of neural networks, this type of crime has become even more dangerous: it has become easier to find information about a person, as well as to forge documents.
We'll tell you where attackers get their data, how they can use it, and how to protect themselves from it.
What you will learn from the article
How doxing came about and how it works now
The very concept of doxing and its methods have changed along with the development of the Internet. Over time, the phenomenon has gone from an ultimatum argument in an online dispute to a powerful weapon.
Doxing as an Internet phenomenon originated in the 1990s. Back then, the Internet was mostly anonymous. Users communicated on forums and in chats, where registration required a maximum of email, and instead of names there were nicknames. An online quarrel in those days could easily lead to the fact that the participant in the conflict went to the extreme measure-found the name, photo or address of the opponent. And then I posted it online. This completely broke the virtual identity of the opponent, which people built up thanks to complete anonymity. This disclosure in English was called dropping docs, which was shortened to doxxing.
Hackers in those years still did not steal user data en masse. Despite the fact that services that store users ' personal data were not protected very well. Banks, insurance companies, and medical organizations were just learning about digital security, so there were a lot of vulnerabilities in their databases.
Instead, hackers were more likely to dox each other — so they revealed competitors. Later, doxing reached out to journalists if someone did not like the information they published. As a rule, they leaked information about the place of residence, family information, or any private information that, in theory, could harm the victim.
Doxing finally took shape in the Web 2.0 era. Internet users began to cluster around large platforms that requested a lot of data. Social networks hit anonymity hard: people began to indicate their real names, post photos and videos. Online stores have received our delivery addresses. Even the simplest loyalty programs now have access to birth dates.
Another major case that has already affected ordinary users occurred in 2015. Then hackers leaked the data of millions of users of the Canadian dating site Ashley Madison to the network. On it sat people who were looking for a partner for infidelity in secret. After the hack, thousands of people faced blackmail and financial fraud due to the disclosure of personal data.
In 2024, the website of Ashley Madison operates under the slogan "Life is short. Have an affair." The security section is full of obvious and cursory privacy tips like using two-factor authentication. Source: ashleymadison.com
Since the early 2020s, doxing has been increasingly used as a fraud tool. Scammers hack social networks, extract personal photos or correspondence, and threaten victims to send screenshots to other people. For money, they offer to prevent this. Doxing is actively used to harass people with other political views, from other social strata, and even in retaliation for criticism of their favorite musicians and actors.
In this case, deanon may be an unintentional crime. One of the most famous cases occurred in 2013 after the terrorist attack during the Boston Marathon. The tragedy quickly united thousands of Reddit users who wanted to help the FBI find the organizers. Moreover, the US authorities published murky photos of the suspects. An analysis of thousands of images and videos led users to the alleged terrorist, Brown University student Sunil Tripathi. Shortly before the attack, the suspect left the house and did not return.
As a result, information about this was spread on the Internet and the media, and the guy's parents began to write that he was a terrorist. Users occupied the Tripathi search pages in social networks. A few days later, the FBI announced that the Tsarnaev brothers were the terrorists. And Tripathi's body was found in the river — he committed suicide before doxing, but this became a black page in Reddit history.
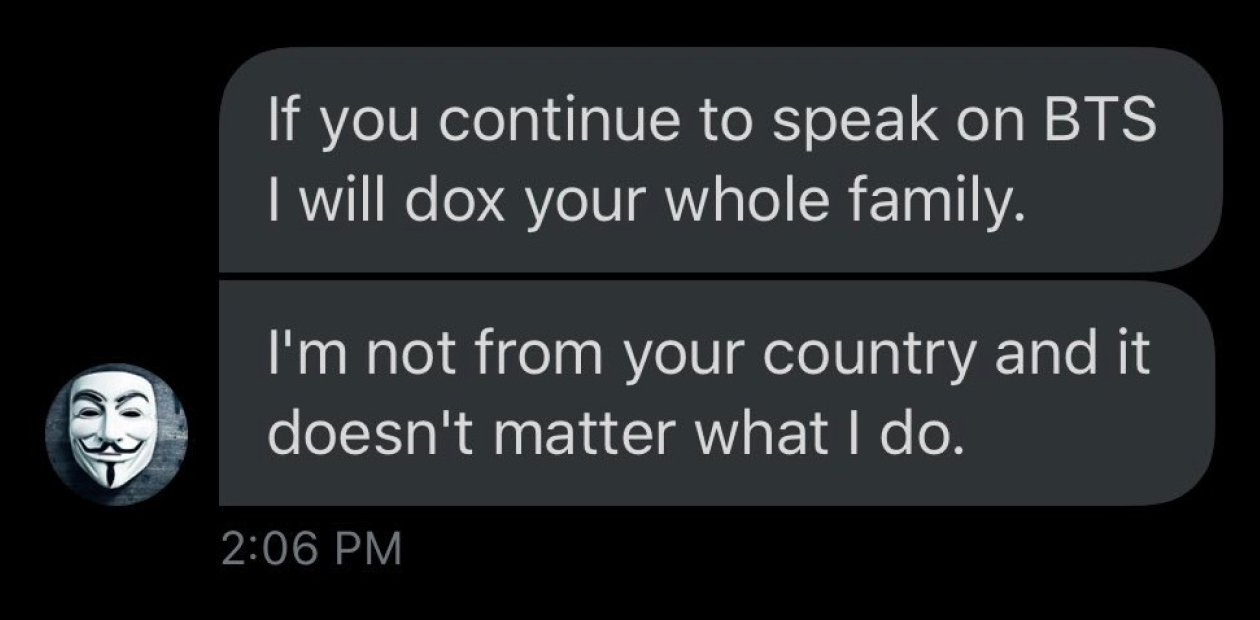
Anonymous radical k-pop fans often threaten journalists for criticizing their favorite artists or start conflicts with other fans. In the screenshot, the doxer promises to post information about the victim's family. Source: southsonder.com
As in many areas, the future of doxing is associated with neural networks and AI. Developers of neural networks prohibit users from violating the law in any way and passing off the results of generation as made by a person. In practice, this is not yet controlled in any way.
There are tools on the Internet that can be used to forge high-quality documents. They have been forged manually for a long time, but this is done by people with certain skills, at least a good knowledge of photo editors. Machine learning tools and neural networks simplify the process for attackers with any skill level.

Crypto traders are faced with fake documents made by AI. Any major crypto exchange requires a passport when registering. The AI inserts the photo and edits the data point-by-point so that the system automatically recognizes the document. Source: cointelegraph.com
In 2023, there are several language models that can be used for doxing. For example, a chatbot generates realistic emails from banks or government agencies ostensibly to clarify information. This is how the victim gives private data to the fraudster.
Neural networks can also be used to generate fake documents — for example, about the ownership of transport or place of residence — and post the information on the Internet. If there is an unorganized group of doxers, such a fake can provoke intruders to cause harm to strangers.
These same bots can also be used for good: information security specialists can study them and create counteraction methods.
What is doxing?
Doxing violates a person's privacy. The more information an attacker learns about a victim, the more problems they can create. At the same time, you can suffer from doxing not only on the web, but also in real life.
Бытовой Household doxing. This is bullying and harassment based on emotions. The most common scenario: a quarrel in an online game or in the comments on a news site. The task of the attacker is to cause psychological damage to the victim, causing anxiety and fear for life.
Bullying can involve former spouses, rejected suitors, badly separated business partners and participants in minor domestic conflicts. In this case, even an ordinary person can become a doxer and organize public harassment.
Information can be thrown anywhere, for example, in social networks or chats. It is difficult to deal with such doxing, because attackers are addicted to stalking and try to completely destabilize the victim. Such harassment often leads to serious consequences.
For example, disclosing just one home address triggers several scenarios. For example, the apartment may be repeatedly knocked on or sent there by couriers. In some cases, a group of law enforcement officers is called to the victim's address, allegedly a crime is taking place in the apartment or house. In the US, the phenomenon is called swatting from the name of the police rapid response unit SWAT. Both ordinary people and public figures suffer from such challenges.
Reputation doxing. This is harassment and harassment of the victim in order to cause her reputational damage. Here, the doxer's goals can be anything: blackmail with the demand for payments to delete information, refuse a transaction, or any other professional activity.
This is usually a custom job for a professional docker. Such an attack is ordered by unscrupulous business partners or competitors. Officials and politicians are often subject to such doxing. Sometimes pop culture stars are engaged in reputation harassment, and some bloggers have a feud with elements of doxing for years.
Doxing is sometimes done by YouTube stars. Blogger SSSniperWolf strangled a Jackfilms blogger, who criticized her for monotonous and borrowed content. Source: LegalEagle YouTube channel
When reputation doxing, they look for information, most often from the past, that can compromise a person. These can be photos of an athlete with alcohol or evidence of the nepotism of a major official. The attacker is interested in information about real estate, cars or any other assets, the publication of which can denigrate a person.
In this case, the sources of stuffing can be closed industry or, conversely, popular news Telegram channels or sites. Such information cannot be unequivocally called defamation, so it can become a serious problem for the victim.
 Corporate doxing. Usually, the targets are specific people or assets that are being targeted, but thousands of random people can become collateral victims.
Corporate doxing. Usually, the targets are specific people or assets that are being targeted, but thousands of random people can become collateral victims.
Because of such actions, the company may go bankrupt, which will lead to layoffs or loss of money by depositors. This is similar to reputation doxing with modifications.
Usually, the scenario is this: disclose information about the real state of a business in order to cause damage. For example, so that a startup doesn't receive funding or the organization stops working due to lawsuits. In this case, doxers can compile real enterprise documents with fake ones in order to confuse partners.
Where do they get information for doxing?
The first cases of doxing were limited to hacking banking systems, calculating the victim's IP address, and using the WHOIS network protocol . Later, store databases, phone and address directories were added to the sources, which people filled out on their own initiative to receive bonus and discount cards.
Now there is so much information that you can make a whole digital portrait of the victim. And the set of personal data is enriched — this is the name of the process when databases are supplemented with new information from different sources. I will list the main ones.
 Social networks. According to research, at the beginning of 2023, more than 73% of Russians used social networks. More than 30% of respondents admitted that they shared their phone number, home address, or workplace information.
Social networks. According to research, at the beginning of 2023, more than 73% of Russians used social networks. More than 30% of respondents admitted that they shared their phone number, home address, or workplace information.
All this data is processed by fraudsters. This is done not manually, but with the help of crawlers . This way you can process thousands of pages a day and create a database from them. There are both closed — for sale — and open databases.
Some old photos, facts from your biography, or personal data may interfere with your life. For example, a potential employer will Google the candidate's name and get to The Dirty website. There, in addition to open data, they collect rumors about ordinary people, which anyone can write and send. You can delete information about yourself from such database sites, but, of course, for money.
Leaks and the darknet. In Russia, mass leaks of personal data occur several times a year. They occurduetargeted attacks on the infrastructure, deliberate insider actions, or technical errors. Companies do not always disclose the causes of leaks, promising to investigate and prevent incidents in the future. But the job is done, the information has got into the network — and you will not be able to reverse this process.
Scammers start using the merged databases for their own purposes. The information can be combined with other leaks, obtaining an even more complete dossier of the victim. The new database may contain your full name, delivery address, and, for example, vehicle information. This gives the doxer complete freedom of action for manipulation: the more data, the more scenarios for doxing.
Also, the doxer can take advantage of the breakdown. This is what is called the disclosure of confidential data about a person for a fee. Sources can be:
Punching services in Russia cost from a thousand rubles for simple information and up to hundreds of thousands for detailed dossiers. Employees who sell user data are regularly arrested, but sometimes they commit crimes again.
 ️
️  ️ Phishing. If the doxer can't find the victim's data in open sources, or the breakdown didn't give the desired result, the criminal can organize a phishing attack. In a simple scenario, an email is created with a request for clarification of data allegedly from the bank.
️ Phishing. If the doxer can't find the victim's data in open sources, or the breakdown didn't give the desired result, the criminal can organize a phishing attack. In a simple scenario, an email is created with a request for clarification of data allegedly from the bank.
The doxer starts an email similar to the official one, copies the real email from the bank and sends it to the victim. To be convincing, attackers can insert a link to some new law or other information guide to confuse the person.
In more complex cases, the scam artist inserts an infected link into the email. The victim can go through it and enter some of their own data. Doxers also actively use instant messengers, although online stores and banks are less likely to use this method of communicating with the client.
How legislation protects against doxing
Each country has its own special features of protection against disclosure of personal data of users. The first laws protecting against online harassment appeared in the United States in the early 2000s. The norms of the law were associated with restraining orders. This is a document that prohibits the attacker from certain actions: approaching the victim, calling her, visiting places and events at the same time as the victim.
The Criminal Code and Administrative Code of the Russian Federation do not contain separate articles related to doxing. At the same time, doxers can be brought to justice — including for violating privacy, extortion, and fraud.
What is the penalty for doxing?
The Criminal Code of the Russian Federation directly links the responsibility of doxers with the goals they pursued, and with the damage they caused.
Criminal liability is provided for the very fact of collecting or distributing information about a person's private life that constitutes his or her personal or family secret without his or her consent . Possible sanctions range from a fine to two years ' imprisonment. Distribution is understood as the disclosure of information about a person's private life in any way — including through the Internet .
But that's not all the trouble that can wait for doxer. It all depends on the goals that he pursues.
For example, if he started demanding money for non-disclosure of information, you can open a criminal case for extortion . A crime is considered to be committed at the time when the doxer demanded money, even if it was not paid. Sanctions range from restriction of freedom for four years to imprisonment for the same period.
It is also considered a crime to forge documents using data from a doxer — for example, to obtain a loan. Sanctions range from a fine to restriction of freedom for two years.
If the doxer threatens to kill or injure the victim and it seems real to the victim, the attacker can be held accountable for threatening to kill or cause serious harm to health. For this, you can already be imprisoned for two years.
To initiate a criminal case, you need to file a statement with the police. The law allows you to do this under several articles of the Criminal Code at once, depending on what exactly the doxer did and what he was trying to achieve.
If the doxer's actions caused damage — for example, a door to an apartment is damaged, a car is burned, or windows are broken-the person responsible will have to pay for it. You can recover damages in a criminal case. You will not have to pay the state fee , you do not need to file a separate claim, and instead of a lawyer, the interests of the victim will be represented in court by a prosecutor.
How to protect yourself from doxing on your own
Saving yourself from disclosing confidential information on the Internet is difficult. The main problem is the information accumulated in databases. This is especially true for those who have been using the same phone number for many years. This is how most systems identify users.
Until the mid-2010s, many personal data operators did not bother to protect themselves, so leaks occurred especially often. Now the situation is not much better, so you should follow some rules of digital hygiene.
Doxing is annoying for many people, so you can contact the administration with a request to remove information from the resource. This won't help if the attacker has already copied the data, but it will at least stop distributing it.
Take care of your social media privacy. It is best not to give too much information about yourself, especially if you know that you have detractors. Just in case, you should delete old profiles in irrelevant social networks and forums. Even abandoned sites can be accessed decades later and still store sensitive data.
If you have already encountered doxing, large social networks have an option to "Complain" about a post or message: Vkontakte, X and Telegram have such options. Usually, platforms accept complaints about the disclosure of personal information, but not all requests for content removal are approved. Also, since 2016, there is a so-called Right to Oblivion in Russia.
Deleting information about yourself from the Internet is not easy
The right to be forgotten is the right of a person to request the removal of information about themselves from the Internet. In the case of doxing, you can request the deletion of data that is distributed in violation of the law or may cause harm — for example, information about the car number or residential address . To do this, contact a specific service or the administration of the site where the information is posted.
But the requirements will need to be supported by evidence — and this can be difficult. And there is no guarantee that the information will be completely deleted. It can be saved on other sites that the user doesn't know about.
Use different credentials for different systems. It is convenient when all forums, social networks, and instant messengers have the same username and password. This makes life easier not only for the user, but also for the doxer. An attacker will be able to track actions by detecting the same or similar nickname on a profile forum, where the user can reveal some new information about themselves.
Use strong passwords. Strong passwords usually consist of at least 12-14 characters, including uppercase, lowercase letters, numbers, and special characters. A good password can be generated in one of a dozen services — most of them are free. The user must specify the desired parameters, and the system will generate a suitable password.
It is also important to use different passwords for different systems. If you have trouble remembering it, you can store the information in the password manager. Most of them are free for individuals.
Create a separate email address for registering accounts. Separate mail for mailing lists and registering with questionable services is a good practice. This will complicate the life of the doxer, who decides to match the identity of the victim and the user from the next leak. It is important to avoid direct linking to yourself: do not use your date of birth or full name in your backup email.
It is also useful to check the email address in the leak databases every few months. Some systems do this automatically. For example, the Chrome browser will tell you that the password you are entering may have been compromised and will prompt you to change it.
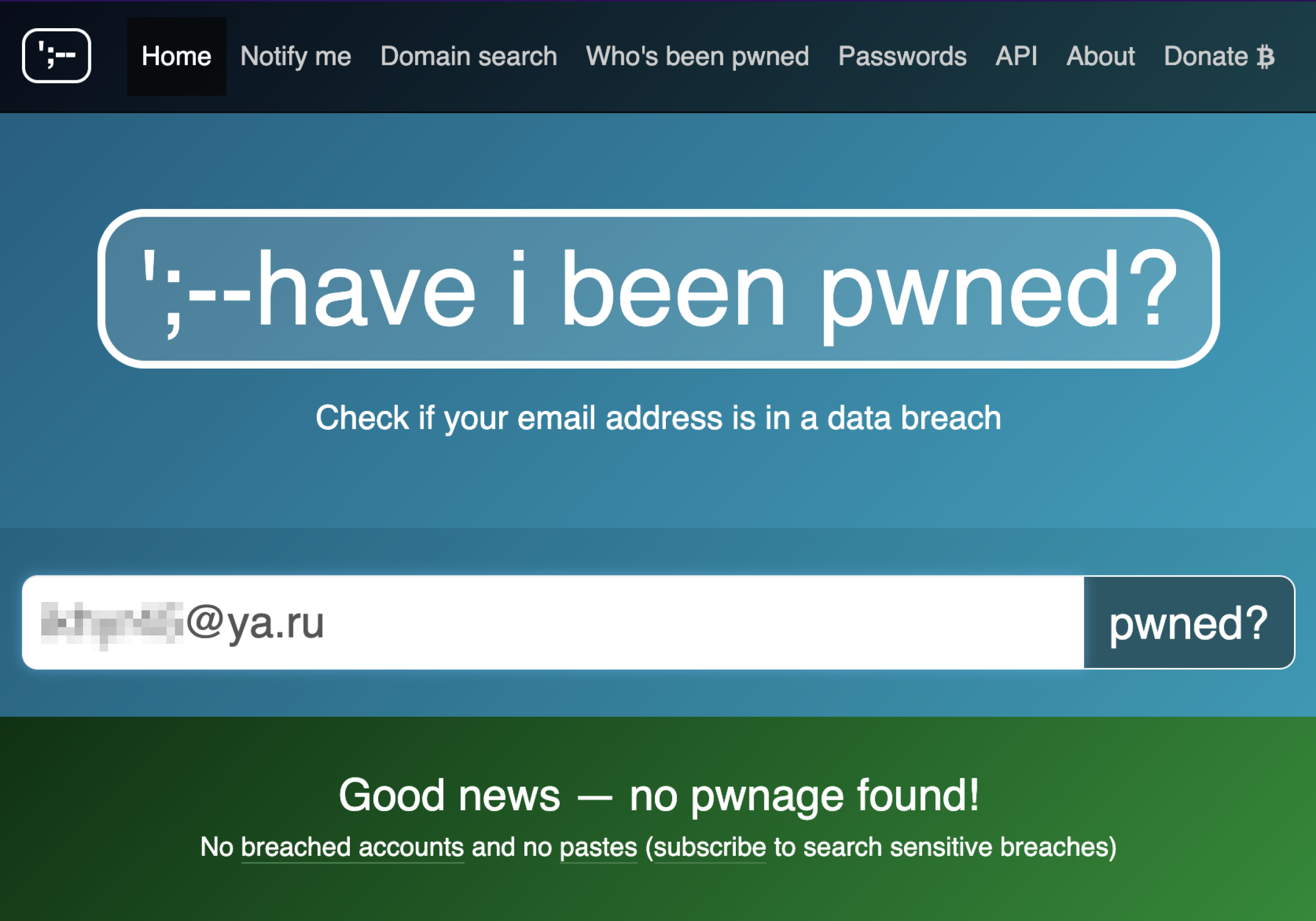
You can check your leaked email for free. Source: haveibeenpwned.com
Use multi-factor authentication. If the doxer somehow finds out your password or login information, such as your passport number, a second identification will help. Sms, push, or email to your backup email address — either method will work. It is important to be consistent and set up the second factor in all key systems.
Regularly update the OS of your gadgets and antivirus programs, and at the same time give up unnecessary programs. Manufacturers release patches that close searchable vulnerabilities. For Windows and Android, it is important to use antivirus protection to block attempts to hack the device or steal information. The antivirus program will also block attempts to click on a malicious link.
If a certain program can be used without registration with minimal inconvenience, it is better to do so. Well, if the program insists on specifying a large amount of data, this is a reason to be wary.
Doxing is the deliberate search and disclosure of information on the Internet about a particular person.
Once upon a time, deanon was already a method of attack in its own right. Gradually, they began to disclose data on the network for the purpose of blackmail, harassment or fraud. Doxing is also often done out of revenge: for example, to former business partners or spouses.
There are many stories on the Internet where a person was bullied by posting information about him in public in social networks, image boards and Telegram channels. And with the development of neural networks, this type of crime has become even more dangerous: it has become easier to find information about a person, as well as to forge documents.
We'll tell you where attackers get their data, how they can use it, and how to protect themselves from it.
What you will learn from the article
- How doxing came about and how it works now
- What is doxing?
- Where do they get information for doxing?
- How legislation protects against doxing
- How to protect yourself from doxing on your own
How doxing came about and how it works now
The very concept of doxing and its methods have changed along with the development of the Internet. Over time, the phenomenon has gone from an ultimatum argument in an online dispute to a powerful weapon.
Doxing as an Internet phenomenon originated in the 1990s. Back then, the Internet was mostly anonymous. Users communicated on forums and in chats, where registration required a maximum of email, and instead of names there were nicknames. An online quarrel in those days could easily lead to the fact that the participant in the conflict went to the extreme measure-found the name, photo or address of the opponent. And then I posted it online. This completely broke the virtual identity of the opponent, which people built up thanks to complete anonymity. This disclosure in English was called dropping docs, which was shortened to doxxing.
Hackers in those years still did not steal user data en masse. Despite the fact that services that store users ' personal data were not protected very well. Banks, insurance companies, and medical organizations were just learning about digital security, so there were a lot of vulnerabilities in their databases.
Instead, hackers were more likely to dox each other — so they revealed competitors. Later, doxing reached out to journalists if someone did not like the information they published. As a rule, they leaked information about the place of residence, family information, or any private information that, in theory, could harm the victim.
Doxing finally took shape in the Web 2.0 era. Internet users began to cluster around large platforms that requested a lot of data. Social networks hit anonymity hard: people began to indicate their real names, post photos and videos. Online stores have received our delivery addresses. Even the simplest loyalty programs now have access to birth dates.
It's not a problem if your name is revealed. But some data can greatly affect your life and career. For example, attackers have already started hunting for private photos and videos. In 2014, there was one of the largest leaks of private photos of American and European celebrities. A huge number of candid pictures appeared on the Web.Then the main risk was no longer the fact of data leakage itself, but its scale and degree of privacy.
Another major case that has already affected ordinary users occurred in 2015. Then hackers leaked the data of millions of users of the Canadian dating site Ashley Madison to the network. On it sat people who were looking for a partner for infidelity in secret. After the hack, thousands of people faced blackmail and financial fraud due to the disclosure of personal data.

In 2024, the website of Ashley Madison operates under the slogan "Life is short. Have an affair." The security section is full of obvious and cursory privacy tips like using two-factor authentication. Source: ashleymadison.com
Since the early 2020s, doxing has been increasingly used as a fraud tool. Scammers hack social networks, extract personal photos or correspondence, and threaten victims to send screenshots to other people. For money, they offer to prevent this. Doxing is actively used to harass people with other political views, from other social strata, and even in retaliation for criticism of their favorite musicians and actors.
In this case, deanon may be an unintentional crime. One of the most famous cases occurred in 2013 after the terrorist attack during the Boston Marathon. The tragedy quickly united thousands of Reddit users who wanted to help the FBI find the organizers. Moreover, the US authorities published murky photos of the suspects. An analysis of thousands of images and videos led users to the alleged terrorist, Brown University student Sunil Tripathi. Shortly before the attack, the suspect left the house and did not return.
As a result, information about this was spread on the Internet and the media, and the guy's parents began to write that he was a terrorist. Users occupied the Tripathi search pages in social networks. A few days later, the FBI announced that the Tsarnaev brothers were the terrorists. And Tripathi's body was found in the river — he committed suicide before doxing, but this became a black page in Reddit history.

Anonymous radical k-pop fans often threaten journalists for criticizing their favorite artists or start conflicts with other fans. In the screenshot, the doxer promises to post information about the victim's family. Source: southsonder.com
As in many areas, the future of doxing is associated with neural networks and AI. Developers of neural networks prohibit users from violating the law in any way and passing off the results of generation as made by a person. In practice, this is not yet controlled in any way.
There are tools on the Internet that can be used to forge high-quality documents. They have been forged manually for a long time, but this is done by people with certain skills, at least a good knowledge of photo editors. Machine learning tools and neural networks simplify the process for attackers with any skill level.

Crypto traders are faced with fake documents made by AI. Any major crypto exchange requires a passport when registering. The AI inserts the photo and edits the data point-by-point so that the system automatically recognizes the document. Source: cointelegraph.com
In 2023, there are several language models that can be used for doxing. For example, a chatbot generates realistic emails from banks or government agencies ostensibly to clarify information. This is how the victim gives private data to the fraudster.
Neural networks can also be used to generate fake documents — for example, about the ownership of transport or place of residence — and post the information on the Internet. If there is an unorganized group of doxers, such a fake can provoke intruders to cause harm to strangers.
These same bots can also be used for good: information security specialists can study them and create counteraction methods.
What is doxing?
Doxing violates a person's privacy. The more information an attacker learns about a victim, the more problems they can create. At the same time, you can suffer from doxing not only on the web, but also in real life.
Бытовой Household doxing. This is bullying and harassment based on emotions. The most common scenario: a quarrel in an online game or in the comments on a news site. The task of the attacker is to cause psychological damage to the victim, causing anxiety and fear for life.
Bullying can involve former spouses, rejected suitors, badly separated business partners and participants in minor domestic conflicts. In this case, even an ordinary person can become a doxer and organize public harassment.
Information can be thrown anywhere, for example, in social networks or chats. It is difficult to deal with such doxing, because attackers are addicted to stalking and try to completely destabilize the victim. Such harassment often leads to serious consequences.
For example, disclosing just one home address triggers several scenarios. For example, the apartment may be repeatedly knocked on or sent there by couriers. In some cases, a group of law enforcement officers is called to the victim's address, allegedly a crime is taking place in the apartment or house. In the US, the phenomenon is called swatting from the name of the police rapid response unit SWAT. Both ordinary people and public figures suffer from such challenges.
Reputation doxing. This is harassment and harassment of the victim in order to cause her reputational damage. Here, the doxer's goals can be anything: blackmail with the demand for payments to delete information, refuse a transaction, or any other professional activity.
This is usually a custom job for a professional docker. Such an attack is ordered by unscrupulous business partners or competitors. Officials and politicians are often subject to such doxing. Sometimes pop culture stars are engaged in reputation harassment, and some bloggers have a feud with elements of doxing for years.
Doxing is sometimes done by YouTube stars. Blogger SSSniperWolf strangled a Jackfilms blogger, who criticized her for monotonous and borrowed content. Source: LegalEagle YouTube channel
When reputation doxing, they look for information, most often from the past, that can compromise a person. These can be photos of an athlete with alcohol or evidence of the nepotism of a major official. The attacker is interested in information about real estate, cars or any other assets, the publication of which can denigrate a person.
In this case, the sources of stuffing can be closed industry or, conversely, popular news Telegram channels or sites. Such information cannot be unequivocally called defamation, so it can become a serious problem for the victim.
Because of such actions, the company may go bankrupt, which will lead to layoffs or loss of money by depositors. This is similar to reputation doxing with modifications.
Usually, the scenario is this: disclose information about the real state of a business in order to cause damage. For example, so that a startup doesn't receive funding or the organization stops working due to lawsuits. In this case, doxers can compile real enterprise documents with fake ones in order to confuse partners.
Where do they get information for doxing?
The first cases of doxing were limited to hacking banking systems, calculating the victim's IP address, and using the WHOIS network protocol . Later, store databases, phone and address directories were added to the sources, which people filled out on their own initiative to receive bonus and discount cards.
Now there is so much information that you can make a whole digital portrait of the victim. And the set of personal data is enriched — this is the name of the process when databases are supplemented with new information from different sources. I will list the main ones.
All this data is processed by fraudsters. This is done not manually, but with the help of crawlers . This way you can process thousands of pages a day and create a database from them. There are both closed — for sale — and open databases.
Some old photos, facts from your biography, or personal data may interfere with your life. For example, a potential employer will Google the candidate's name and get to The Dirty website. There, in addition to open data, they collect rumors about ordinary people, which anyone can write and send. You can delete information about yourself from such database sites, but, of course, for money.
Leaks and the darknet. In Russia, mass leaks of personal data occur several times a year. They occurduetargeted attacks on the infrastructure, deliberate insider actions, or technical errors. Companies do not always disclose the causes of leaks, promising to investigate and prevent incidents in the future. But the job is done, the information has got into the network — and you will not be able to reverse this process.
Scammers start using the merged databases for their own purposes. The information can be combined with other leaks, obtaining an even more complete dossier of the victim. The new database may contain your full name, delivery address, and, for example, vehicle information. This gives the doxer complete freedom of action for manipulation: the more data, the more scenarios for doxing.
Also, the doxer can take advantage of the breakdown. This is what is called the disclosure of confidential data about a person for a fee. Sources can be:
- mobile network operators;
- state information systems;
- banks and other financial institutions.
Punching services in Russia cost from a thousand rubles for simple information and up to hundreds of thousands for detailed dossiers. Employees who sell user data are regularly arrested, but sometimes they commit crimes again.
The doxer starts an email similar to the official one, copies the real email from the bank and sends it to the victim. To be convincing, attackers can insert a link to some new law or other information guide to confuse the person.
In more complex cases, the scam artist inserts an infected link into the email. The victim can go through it and enter some of their own data. Doxers also actively use instant messengers, although online stores and banks are less likely to use this method of communicating with the client.
How legislation protects against doxing
Each country has its own special features of protection against disclosure of personal data of users. The first laws protecting against online harassment appeared in the United States in the early 2000s. The norms of the law were associated with restraining orders. This is a document that prohibits the attacker from certain actions: approaching the victim, calling her, visiting places and events at the same time as the victim.
The Criminal Code and Administrative Code of the Russian Federation do not contain separate articles related to doxing. At the same time, doxers can be brought to justice — including for violating privacy, extortion, and fraud.
What is the penalty for doxing?
The Criminal Code of the Russian Federation directly links the responsibility of doxers with the goals they pursued, and with the damage they caused.
Criminal liability is provided for the very fact of collecting or distributing information about a person's private life that constitutes his or her personal or family secret without his or her consent . Possible sanctions range from a fine to two years ' imprisonment. Distribution is understood as the disclosure of information about a person's private life in any way — including through the Internet .
But that's not all the trouble that can wait for doxer. It all depends on the goals that he pursues.
For example, if he started demanding money for non-disclosure of information, you can open a criminal case for extortion . A crime is considered to be committed at the time when the doxer demanded money, even if it was not paid. Sanctions range from restriction of freedom for four years to imprisonment for the same period.
It is also considered a crime to forge documents using data from a doxer — for example, to obtain a loan. Sanctions range from a fine to restriction of freedom for two years.
If the doxer threatens to kill or injure the victim and it seems real to the victim, the attacker can be held accountable for threatening to kill or cause serious harm to health. For this, you can already be imprisoned for two years.
To initiate a criminal case, you need to file a statement with the police. The law allows you to do this under several articles of the Criminal Code at once, depending on what exactly the doxer did and what he was trying to achieve.
If the doxer's actions caused damage — for example, a door to an apartment is damaged, a car is burned, or windows are broken-the person responsible will have to pay for it. You can recover damages in a criminal case. You will not have to pay the state fee , you do not need to file a separate claim, and instead of a lawyer, the interests of the victim will be represented in court by a prosecutor.
How to protect yourself from doxing on your own
Saving yourself from disclosing confidential information on the Internet is difficult. The main problem is the information accumulated in databases. This is especially true for those who have been using the same phone number for many years. This is how most systems identify users.
Until the mid-2010s, many personal data operators did not bother to protect themselves, so leaks occurred especially often. Now the situation is not much better, so you should follow some rules of digital hygiene.
Doxing is annoying for many people, so you can contact the administration with a request to remove information from the resource. This won't help if the attacker has already copied the data, but it will at least stop distributing it.
Take care of your social media privacy. It is best not to give too much information about yourself, especially if you know that you have detractors. Just in case, you should delete old profiles in irrelevant social networks and forums. Even abandoned sites can be accessed decades later and still store sensitive data.
If you have already encountered doxing, large social networks have an option to "Complain" about a post or message: Vkontakte, X and Telegram have such options. Usually, platforms accept complaints about the disclosure of personal information, but not all requests for content removal are approved. Also, since 2016, there is a so-called Right to Oblivion in Russia.
Deleting information about yourself from the Internet is not easy
The right to be forgotten is the right of a person to request the removal of information about themselves from the Internet. In the case of doxing, you can request the deletion of data that is distributed in violation of the law or may cause harm — for example, information about the car number or residential address . To do this, contact a specific service or the administration of the site where the information is posted.
But the requirements will need to be supported by evidence — and this can be difficult. And there is no guarantee that the information will be completely deleted. It can be saved on other sites that the user doesn't know about.
Use different credentials for different systems. It is convenient when all forums, social networks, and instant messengers have the same username and password. This makes life easier not only for the user, but also for the doxer. An attacker will be able to track actions by detecting the same or similar nickname on a profile forum, where the user can reveal some new information about themselves.
Use strong passwords. Strong passwords usually consist of at least 12-14 characters, including uppercase, lowercase letters, numbers, and special characters. A good password can be generated in one of a dozen services — most of them are free. The user must specify the desired parameters, and the system will generate a suitable password.
It is also important to use different passwords for different systems. If you have trouble remembering it, you can store the information in the password manager. Most of them are free for individuals.
Create a separate email address for registering accounts. Separate mail for mailing lists and registering with questionable services is a good practice. This will complicate the life of the doxer, who decides to match the identity of the victim and the user from the next leak. It is important to avoid direct linking to yourself: do not use your date of birth or full name in your backup email.
It is also useful to check the email address in the leak databases every few months. Some systems do this automatically. For example, the Chrome browser will tell you that the password you are entering may have been compromised and will prompt you to change it.

You can check your leaked email for free. Source: haveibeenpwned.com
Use multi-factor authentication. If the doxer somehow finds out your password or login information, such as your passport number, a second identification will help. Sms, push, or email to your backup email address — either method will work. It is important to be consistent and set up the second factor in all key systems.
Regularly update the OS of your gadgets and antivirus programs, and at the same time give up unnecessary programs. Manufacturers release patches that close searchable vulnerabilities. For Windows and Android, it is important to use antivirus protection to block attempts to hack the device or steal information. The antivirus program will also block attempts to click on a malicious link.
If a certain program can be used without registration with minimal inconvenience, it is better to do so. Well, if the program insists on specifying a large amount of data, this is a reason to be wary.













