- Joined
- Dec 3, 2020
- Messages
- 1,738
Check Point Exploration (CPR) as of late covered a live programming administration, named TrickGate, that has been involved by vindictive danger entertainers for north of six years. TrickGate is basically a packer that permits cybercriminals to do noxious exercises, for example, conveying malignant code by sidestepping antivirus checks.
As per specialists, there are a couple of central issues that permit a packer, for example, TrickGate to stay effective and imperceptible for such countless years.
Initial, a packer can contain any sort of payload, and since it isn't restricted to any single one, it can likewise be utilized to pack various vindictive examples.
Furthermore, a packer's intrinsic nature takes into consideration changes to its covering consistently, which empowers it to dodge discovery from security items.
In any case, CPR had the option to come to an obvious conclusion from earlier exploration and wound up observing a solitary activity that gave off an impression of being presented as a help. Their exploration recommends that various danger entertainers from gatherings, for example, Cerberus, Emotet, REvil, Labyrinth, Cerber, HawkEye, AZORult, Formbook, Remcos, LokiBit, AgentTesla and more took advantage of the assistance to send malware.
The warning further gauges that, during the most recent two years, danger entertainers have utilized TrickGate to direct 40 to 60 assaults each week. The significantly designated industry was fabricating, yet others like training, medical services, money, and business undertakings were additionally impacted.
"The assaults are appropriated everywhere, with an expanded focus in Taiwan and Turkey. The most well known malware family utilized over the most recent 2 months is Formbook with 42% of the all out followed appropriation," CPR wrote in its report.
Going into specialized profundity, CPR security scientist Arie Olshtein made sense of that the whole assault stream of TrickGate shows that the malevolent program is first encoded and afterward loaded with a unique daily practice. It is intended to keep the framework from distinguishing the payload statically and at run-time.
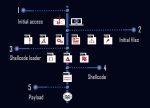
CPR's warning closes with the requirement for more thoughtfulness regarding disentangling the packer's structure blocks since they give a method for identifying the danger at a beginning phase. The best way to handle a programmer's groundbreaking skills is by offering them the very consideration that is given to genuine malware. Scientists can now utilize the recognized packer, TrickGate, as a point of convergence to distinguish new or obscure malware.
As per specialists, there are a couple of central issues that permit a packer, for example, TrickGate to stay effective and imperceptible for such countless years.
Initial, a packer can contain any sort of payload, and since it isn't restricted to any single one, it can likewise be utilized to pack various vindictive examples.
Furthermore, a packer's intrinsic nature takes into consideration changes to its covering consistently, which empowers it to dodge discovery from security items.
In any case, CPR had the option to come to an obvious conclusion from earlier exploration and wound up observing a solitary activity that gave off an impression of being presented as a help. Their exploration recommends that various danger entertainers from gatherings, for example, Cerberus, Emotet, REvil, Labyrinth, Cerber, HawkEye, AZORult, Formbook, Remcos, LokiBit, AgentTesla and more took advantage of the assistance to send malware.
The warning further gauges that, during the most recent two years, danger entertainers have utilized TrickGate to direct 40 to 60 assaults each week. The significantly designated industry was fabricating, yet others like training, medical services, money, and business undertakings were additionally impacted.
"The assaults are appropriated everywhere, with an expanded focus in Taiwan and Turkey. The most well known malware family utilized over the most recent 2 months is Formbook with 42% of the all out followed appropriation," CPR wrote in its report.
Going into specialized profundity, CPR security scientist Arie Olshtein made sense of that the whole assault stream of TrickGate shows that the malevolent program is first encoded and afterward loaded with a unique daily practice. It is intended to keep the framework from distinguishing the payload statically and at run-time.

CPR's warning closes with the requirement for more thoughtfulness regarding disentangling the packer's structure blocks since they give a method for identifying the danger at a beginning phase. The best way to handle a programmer's groundbreaking skills is by offering them the very consideration that is given to genuine malware. Scientists can now utilize the recognized packer, TrickGate, as a point of convergence to distinguish new or obscure malware.













