- Joined
- Nov 26, 2020
- Messages
- 716

I recently received a batch of files found in an infected POS system (POS system hacked due to weak rdp password)
Interface of a hacked POS card used by a jeweler:
out.exe is the Ardamax (ardamax.com) keylogger, and vui qua.exe is an SFX archive that displays this image when launched:

And throw the perfect keylogger (blazingtools.com) back.
"vui qua" may be a Vietnamese phrase that translates to "so funny."
These two keyloggers are probably useless for a carder, here is an interesting file "mmon.exe" a ram scraper.
It scans each process looking for CC dumps that were written to memory tracks 1, 2.
If the POS device is connected to the computer, it will immediately receive its card details.
How? POS terminals always use end-to-end encryption, the only place where it is not encrypted is the internal memory.
But.. memory capacity is limited, so data is constantly being overwritten.
This is also a problem for mmon, because this crap does not have a looping function and does not write inside a file.
POS carders usually use better malware than this, but this is what I got...
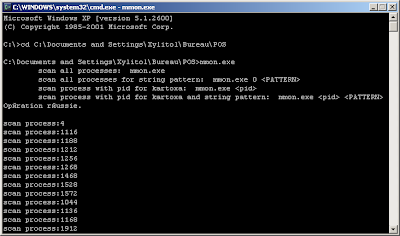
(mmon.exe "Kartoxa" is probably a corrupted version of the word "potato")
mmon scanning process.
mmon test with a valid second track in memory
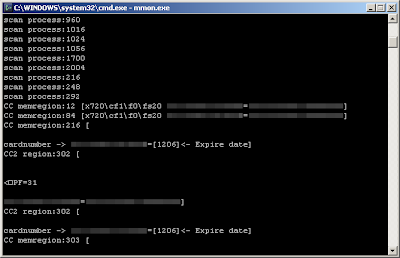
When a dump is detected, the program does nothing with it, it simply prints the contents to the console.
The bad guys simply connect to the POS terminal via RDP, receive the dumps via mmon and write them to a magnetic stripe using a card writer.

(USB Magnetic Stripe Reader/Encoder MSR606)
Then use the embosser to stamp the printed numbers onto the card.

(DXR 70C embosser)
And it's ready to use... in the US (Type 101)
We have 201 cards (pin and chip) in Europe.
The 101 just needs to be swiped in the store and the cashier will check the last 4 digits on the card if they are true.
Carders also use printers such as Fargo to produce fake IDs.
Either way, POS malware comes with a high price tag and it's not a business that anyone can get into.













