Premiums
TRUSTED VENDOR
- Joined
- Dec 5, 2020
- Messages
- 3,206
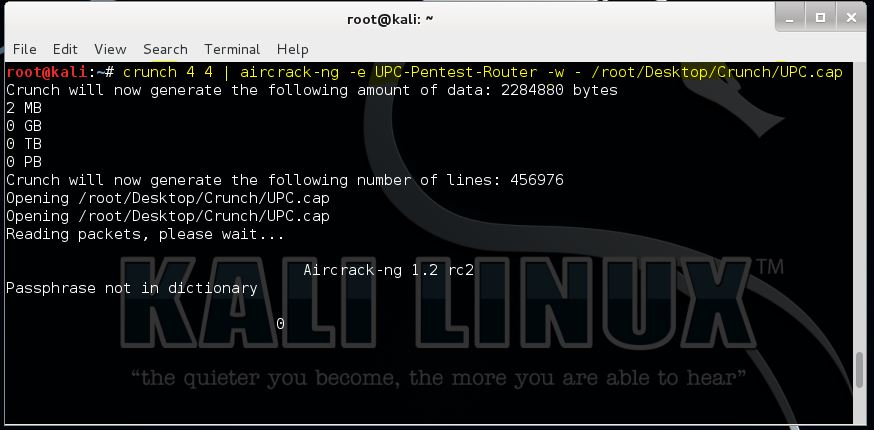
In this new hacking tutorial we will be Piping Crunch with Aircrack-ng so we can get rid of the constantly increasing dictionary files used to retrieve WiFi passwords from cap files. When we pipe the output from Crunch with Aircrack-ng the data will be fed directly into Aircrack-ng instead of a text file. Aircrack-ng will be using the input from Crunch for brute forcing the password. This method will safe us a lot of time and valuable drive space since effective wordlists for brute forcing purposes tend to grow very fast in a short time.
Piping Crunch with Aircrack-ng
After we’ve captured the 4 way handshake, which we will not be covering in this tutorial, we can pipe Crunch with Aircrack-ng to break the password. The following tutorials will teach you how to capture handshakes using the aircrack-ng software suite in Kali Linux:
- The Top 10 Wifi Hacking Tools in Kali Linux
- Pixie Dust Attack WPS in Kali Linux with Reaver
- How to hack a TP link WR841N router wireless network
Please note that the file paths used in this command are case sensitive and the | sign which is actually piping Crunch with Aircrack-ng.
crunch 8 8 | aircrack-ng -e [ESSID] -w – [file path to the .cap file]
Crunch Tutorial
Crunch in Kali Linux has serveral features to generate passwords from which only one of them is used in this tutorial. The following tutorial is about how to use the different options in Crunch to generate the password list you need, for example a default router password containing 8 letters (like UPC Broadband) or the use of static sequences of text and numbers:
Crunch Password list generation in Kali Linux
Thanks for reading and do not hesitate to ask any questions related to this hacking tutorial in the comment section




















