Premiums
TRUSTED VENDOR
- Joined
- Dec 5, 2020
- Messages
- 1,347
I have Break The security(BTS) readers, this is first Backtrack 4 hacking tutorial. Today let us see about the HashCat cracking tool(Dictionary attack). if you don’t know what is Dictionary attack,then please read this Dictionary Attack Practical Example
Backtrack 4 Tutorials Step 1:
Boot into the Backtrack 4 Linux.
Now Navigate to this Path:
Backtrack->privilege Escalation->Password attack->Offline attacks
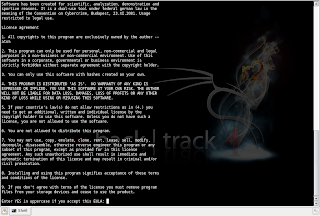
Open the HashCat .
Now you can see the terminal window with this path :
root@bt:/pentest/passwords/hashcat#
Step 2:
If you scroll to the top, you will find helpful commands. The standard format to run the hashcat application is
./hashcat-cli.bin [options] hashfile [wordfiles|directories]
You can see the list of options below the command format.
Hash files is file which contains the hashcode(MD5 Hash code for instance).
worldfiles is dictionary file
List of optiions are:
Startup:
Copy the dictionary file and hashcode file to desktop.
I have this MD5 hashcode (c3ea886e7d47f5c49a7d092fadf0c03b) inside the hash.txt file.
My dictionary file is english.txt

Step 4:
now type this command:
/hashcat-cli.bin ‘/root/hash.txt’ ‘/root/english.txt’
and hit enter now hashcode will be cracked.
NOTE:
If you are running the Hashcat for first time,then you will get this
“EULA has changed,need to restart the hashcat”.
Just close the window and open the hashcat, then run the above command.
Step 5:
if you can not crack with above method itself,then proceed with this.
You can enhance the cracking by using options.
HashMode Option:
Using Hashmode we can specify which type of Hash code we are going to crack.
How to use Hashmode option?
‘-m[value]’ is to specify the hashmode method.
Refer the above list of option to know the different values of hashmode.
We are going to crack MD5 Hashcode,right? for md5 ,value is 0.
So use this command:
/hashcat-cli.bin -m0 ‘/root/hash.txt’ ‘/root/english.txt’
Enhancing with Attack Mode(-a[value]):
Using attack mode,we can specify how the password can be. I think you may not understand what i am saying. So i will explain the attack mode with example.
ok lets take the simple key “iloveyou” from english.txt.
Values of Attack Mode are:
0 = Straight
1 = Combination
2 = Toggle-Case
3 = Brute-Force
4 = Permutation
if we use -a0 option,then key will as it is ” iloveyou”. for -a1,it will be “iloveyouiloveyou”. for -a2 ,it will be IloveYou,ILoveyou..etc. I think you know about brute force,if you don’t know please read my previous post about bruteforce. I hope you know about permutation.
/hashcat-cli.bin -m0 -a2 ‘/root/hash.txt’ ‘/root/english.txt’
Backtrack 4 Tutorials Step 1:
Boot into the Backtrack 4 Linux.
Now Navigate to this Path:
Backtrack->privilege Escalation->Password attack->Offline attacks
Open the HashCat .
Now you can see the terminal window with this path :
root@bt:/pentest/passwords/hashcat#
Step 2:
If you scroll to the top, you will find helpful commands. The standard format to run the hashcat application is
./hashcat-cli.bin [options] hashfile [wordfiles|directories]
You can see the list of options below the command format.
Hash files is file which contains the hashcode(MD5 Hash code for instance).
worldfiles is dictionary file
List of optiions are:
Startup:
Step 3:-V, –version print version
-h, –help print help
–eula print eula
Logging and Files:
-r, –rules-file=FILE rules-file for hybrid-attack
-o, –output-file=FILE output-file for recovered hashes
-e, –salt-file=FILE salts-file for unsalted hashlists
–debug-file=FILE debug-file
–debug-mode=NUM 0 = save finding rule (hybrid only)
1 = save original word (hybrid only)
2 = save recovered pass
-p, –seperator-char=CHAR seperator-char for hashlists
Resources:
-n, –threads=NUM number of threads
-c, –segment-size=NUM number of mb to cache from wordfile
-s, –words-skip=NUM skip number of words (for resume)
-l, –words-limit=NUM limit number of words (for distributed)
Attacks:
-g, –generate-rules=NUM number of self-generating rules
–generate-rules-func-min=NUM force number of functions per rule min
–generate-rules-func-max=NUM force number of functions per rule max
-a, –attack-mode=NUM number of attack-mode
0 = Straight *
1 = Combination *
2 = Toggle-Case *
3 = Brute-Force
4 = Permutation
* = for Hybrid-Attack use -r or -g
-m, –hash-mode=NUM number of hash-mode
0 = MD5 200 = MySQL
1 = md5($pass.$salt) 300 = MySQL4.1/MySQL5
2 = md5($salt.$pass) 400 = MD5(WordPress)
3 = md5(md5($pass)) 400 = MD5(phpBB3)
4 = md5(md5(md5($pass))) 500 = MD5(Unix)
5 = md5(md5($pass).$salt) 600 = SHA-1(Base64)
6 = md5(md5($salt).$pass) 700 = SSHA-1(Base64)
7 = md5($salt.md5($pass)) 800 = SHA-1(Django)
8 = md5($salt.$pass.$salt) 900 = MD4
9 = md5(md5($salt).md5($pass)) 1000 = NTLM
10 = md5(md5($pass).md5($salt)) 1100 = Domain Cached Credentials
11 = md5($salt.md5($salt.$pass)) 1200 = MD5(Chap)
12 = md5($salt.md5($pass.$salt)) 1300 = MSSQL
30 = md5($username.0.$pass)
31 = md5(strtoupper(md5($pass)))
100 = SHA1
101 = sha1($pass.$salt)
102 = sha1($salt.$pass)
103 = sha1(sha1($pass))
104 = sha1(sha1(sha1($pass)))
105 = sha1(strtolower($username).$pass)
Toggle-Case specific:
–toggle-min=NUM number of alphas in plain minimum
–toggle-max=NUM number of alphas in plain maximum
Brute-Force specific:
–bf-pw-min=NUM password length minimum
–bf-pw-max=NUM password length maximum
–bf-cs-buf=CHARS charset for attack
Permutation specific:
–perm-min=NUM number of chars in plain minimum
–perm-max=NUM number of chars in plain maximum
Copy the dictionary file and hashcode file to desktop.
I have this MD5 hashcode (c3ea886e7d47f5c49a7d092fadf0c03b) inside the hash.txt file.
My dictionary file is english.txt

Step 4:
now type this command:
/hashcat-cli.bin ‘/root/hash.txt’ ‘/root/english.txt’
and hit enter now hashcode will be cracked.
NOTE:
If you are running the Hashcat for first time,then you will get this
“EULA has changed,need to restart the hashcat”.
Just close the window and open the hashcat, then run the above command.
Step 5:
if you can not crack with above method itself,then proceed with this.
You can enhance the cracking by using options.
HashMode Option:
Using Hashmode we can specify which type of Hash code we are going to crack.
How to use Hashmode option?
‘-m[value]’ is to specify the hashmode method.
Refer the above list of option to know the different values of hashmode.
We are going to crack MD5 Hashcode,right? for md5 ,value is 0.
So use this command:
/hashcat-cli.bin -m0 ‘/root/hash.txt’ ‘/root/english.txt’
Enhancing with Attack Mode(-a[value]):
Using attack mode,we can specify how the password can be. I think you may not understand what i am saying. So i will explain the attack mode with example.
ok lets take the simple key “iloveyou” from english.txt.
Values of Attack Mode are:
0 = Straight
1 = Combination
2 = Toggle-Case
3 = Brute-Force
4 = Permutation
if we use -a0 option,then key will as it is ” iloveyou”. for -a1,it will be “iloveyouiloveyou”. for -a2 ,it will be IloveYou,ILoveyou..etc. I think you know about brute force,if you don’t know please read my previous post about bruteforce. I hope you know about permutation.
/hashcat-cli.bin -m0 -a2 ‘/root/hash.txt’ ‘/root/english.txt’