Using VPN, TOR or even Tails, you think your anonymity is protected. Unfortunately, this is not the case. There is one very important channel for leaking your private information - the DNS service. But fortunately, a solution has been invented for this too. Today I will show you how to encrypt your DNS traffic using the DNSCrypt utility. Go!
When using HTTPS or SSL, your HTTP traffic is encrypted, that is, protected. When you use a VPN, all your traffic is already encrypted (of course, it all depends on the VPN settings, but, as a rule, it is). But sometimes, even when using a VPN, your DNS requests are not encrypted, they are transmitted as-is, which opens up a huge space for "creativity", including MITM attacks, traffic redirection and much more.
This is where the open source DNSCrypt utility comes to the rescue, developed by the creators of OpenDNS, well known to you, - a program that allows you to encrypt DNS requests. After installing it on your computer, your connections will also be protected and you will be able to surf the Internet more securely. Of course, DNSCrypt is not a panacea for all problems, but only one of the security tools. You still need to use a VPN connection to encrypt all traffic, but it will be safer when paired with DNSCrypt. If you are satisfied with such a short explanation, you can go straight to the section where I will describe the installation and use of the program.
Let's try to understand deeper. As they say, it is better to see once than hear a hundred times. Look at the drawing.
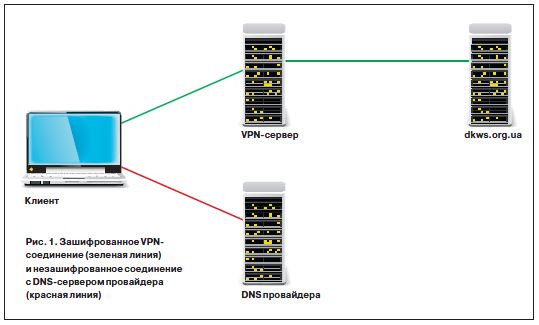
How DNSCrypt works
Let's say a client (laptop in the picture) tries to access google.com The first step is to resolve the symbolic hostname to an IP address. If the network configuration is such that the provider's DNS server is used (unencrypted connection, red line in the figure), then the symbolic name is resolved into an IP address over an unencrypted connection.
Yes, no one will know what data you will transfer to dkws.org.ua. But there are some very unpleasant moments. First, the provider, by looking at the DNS logs, will be able to find out which sites you have visited. Do you need it? Secondly, the possibility of attacks is likely: DNS spoofing and DNS snooping. I will not describe them in detail, many articles have already been written about this. In a nutshell, the situation can be as follows: someone between you and the provider can intercept the DNS request (and since the requests are not encrypted, it will not be difficult to intercept the request and read its contents) and send you a “fake” response. As a result, instead of visiting google.com, you will go to the attacker's site, like two peas in a pod similar to the one you need, enter your password from the forum, and then the development of events, I think, is clear.

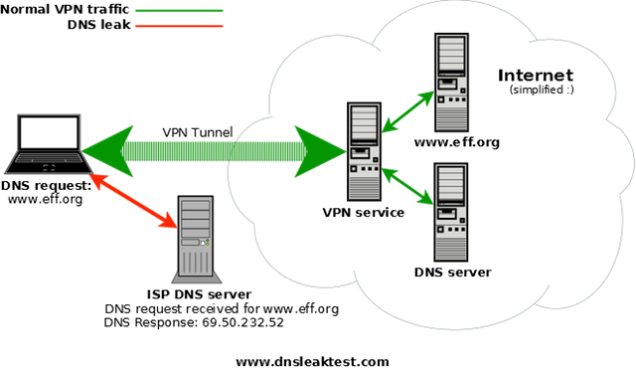
This situation is called DNS leaking . DNS leaking occurs when your system, even after connecting to a VPN server or Tor, continues to query the provider's DNS servers to resolve domain names. Every time you visit a new site, connect to a new server or launch some kind of network application, your system turns to the DNS provider to resolve the name to IP. As a result, your ISP or anyone who is on the "last mile", that is, between you and the ISP, can get all the names of the nodes you are accessing. The above option with spoofing the IP address is completely cruel, but in any case, it is possible to track the sites you visited and use this information for your own purposes.
If you are "afraid" of your ISP or just do not want him to see what sites you visit, you can (of course, besides using VPN and other security tools) additionally configure your computer to use the DNS servers of the OpenDNS project (www.opendns.com) ...
At the moment, these are the following servers:
But the problem of intercepting DNS connections still remains. Yes, you are already accessing not the provider's DNS, but OpenDNS, but you can still intercept packets and see what is in them. That is, if you wish, you can find out which nodes you accessed.
So we come to DNSCrypt. This program allows you to encrypt your DNS connection. Now your ISP (and everyone between you and them) will not know exactly which sites you visit! I will repeat myself. This program is not a replacement for Tor or VPN. As before, the rest of the data you transmit is transmitted without encryption if you do not use either VPN or Tor. The program encrypts only DNS traffic.
DNS LEAK
The
DNS Leak Tests
DNS Leak Test is a free tool for the internet allowing end users to test their DNS activity to see if their VPN or Proxy service is leaking DNS requests, effectively unmasking end user's privacy and security.
dnsleak.com
site allows you to identify a DNS "leak". Just go to this site. By clicking the Check for DNS leaks now button, you will receive a list of DNS servers through which your queries can pass. Therefore, you will see exactly who can find out which sites you visit.
INSTALLATION AND USE DNSCRYPT
The easiest way to secure your DNS connection is to use DNSCrypt.
First of all, download DNSCrypt itself from GitHub. To download the program from GitHub, click the Download ZIP button. The archive with the DNSCrypt sources will be downloaded. The already compiled version is in the archive's DNSCrypt directory. Unpack the files. Basically, you only need one file - dnscrypt-proxy.exe. It is located in the same directory. Everything else (sources) can be deleted.
But that's not all. If you've already googled it, then you've seen screenshots of DNSCrypt. By running dnscrypt-proxy.exe, you realized that something was wrong. The program was launched in a command prompt window. That's right, you downloaded the proxy itself, and now you still need to download a shell for it. There is another project on GitHub - the wrapper we need (https://github.com/Noxwizard/dnscrypt-winclient).
Download the ZIP archive in the same way, unpack it somewhere. The binaries / Release / directory contains the dnscrypt-winclient.exe program. Copy this file to the directory containing the dnscrypt-proxy.exe file.
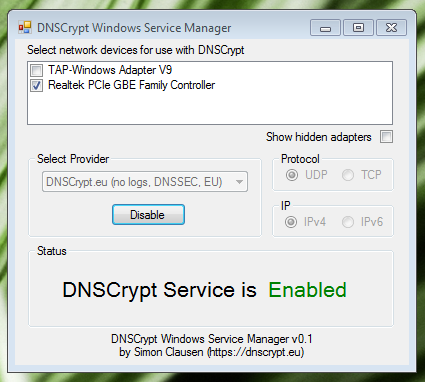
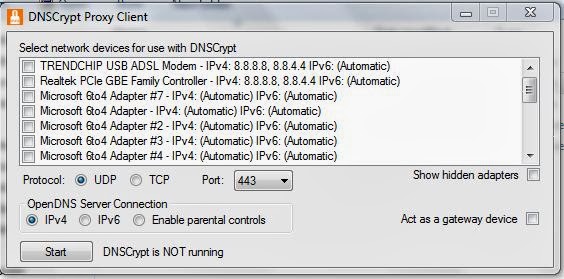
All that remains is to run dnscrypt-proxy.exe. In the window that appears, select the network adapters you want to protect and click the Start button. If everything is normal, then DNSCrypt is running will appear next to the Stop button (the Start button will turn into it).
CONCLUSION
The article turned out to be not very long, since the program itself is very easy to use. But it would be incomplete if I didn’t mention VPN too. If you have read this article, you are interested in it, but you still do not use the services of a VPN provider to encrypt your data, then it's time to do it.
The VPN provider will provide you with a secure tunnel to transfer your data, and DNSCrypt will secure your DNS connections. Of course, the services of VPN providers are paid, but do you have to pay for security?
You can, of course, use Tor, but Tor is relatively slow, and this, whatever one may say, is not a VPN - all traffic cannot be "torified". Either way (whichever option you choose) your DNS connections are now secure. It remains only to decide on a traffic encryption tool (if you have not done it yet).
And in order to save money and not pay such a huge amount of money that VPN providers now take, you can order a VPN for 50% of the cost from @levynson. He has about 10 different VPNs available, but personally, I recommend taking only NordVPN. I hope that this information was useful to you, so I will be grateful if you share the link and this article with your friends and make a repost.

When using HTTPS or SSL, your HTTP traffic is encrypted, that is, protected. When you use a VPN, all your traffic is already encrypted (of course, it all depends on the VPN settings, but, as a rule, it is). But sometimes, even when using a VPN, your DNS requests are not encrypted, they are transmitted as-is, which opens up a huge space for "creativity", including MITM attacks, traffic redirection and much more.
This is where the open source DNSCrypt utility comes to the rescue, developed by the creators of OpenDNS, well known to you, - a program that allows you to encrypt DNS requests. After installing it on your computer, your connections will also be protected and you will be able to surf the Internet more securely. Of course, DNSCrypt is not a panacea for all problems, but only one of the security tools. You still need to use a VPN connection to encrypt all traffic, but it will be safer when paired with DNSCrypt. If you are satisfied with such a short explanation, you can go straight to the section where I will describe the installation and use of the program.
Let's try to understand deeper. As they say, it is better to see once than hear a hundred times. Look at the drawing.

How DNSCrypt works
Let's say a client (laptop in the picture) tries to access google.com The first step is to resolve the symbolic hostname to an IP address. If the network configuration is such that the provider's DNS server is used (unencrypted connection, red line in the figure), then the symbolic name is resolved into an IP address over an unencrypted connection.
Yes, no one will know what data you will transfer to dkws.org.ua. But there are some very unpleasant moments. First, the provider, by looking at the DNS logs, will be able to find out which sites you have visited. Do you need it? Secondly, the possibility of attacks is likely: DNS spoofing and DNS snooping. I will not describe them in detail, many articles have already been written about this. In a nutshell, the situation can be as follows: someone between you and the provider can intercept the DNS request (and since the requests are not encrypted, it will not be difficult to intercept the request and read its contents) and send you a “fake” response. As a result, instead of visiting google.com, you will go to the attacker's site, like two peas in a pod similar to the one you need, enter your password from the forum, and then the development of events, I think, is clear.

This situation is called DNS leaking . DNS leaking occurs when your system, even after connecting to a VPN server or Tor, continues to query the provider's DNS servers to resolve domain names. Every time you visit a new site, connect to a new server or launch some kind of network application, your system turns to the DNS provider to resolve the name to IP. As a result, your ISP or anyone who is on the "last mile", that is, between you and the ISP, can get all the names of the nodes you are accessing. The above option with spoofing the IP address is completely cruel, but in any case, it is possible to track the sites you visited and use this information for your own purposes.
If you are "afraid" of your ISP or just do not want him to see what sites you visit, you can (of course, besides using VPN and other security tools) additionally configure your computer to use the DNS servers of the OpenDNS project (www.opendns.com) ...
At the moment, these are the following servers:
- 87.98.175.85 (ns10.fr): 99.74% uptime
- 130.255.73.90 (ns3.nw.de): 97.45% uptime
But the problem of intercepting DNS connections still remains. Yes, you are already accessing not the provider's DNS, but OpenDNS, but you can still intercept packets and see what is in them. That is, if you wish, you can find out which nodes you accessed.
So we come to DNSCrypt. This program allows you to encrypt your DNS connection. Now your ISP (and everyone between you and them) will not know exactly which sites you visit! I will repeat myself. This program is not a replacement for Tor or VPN. As before, the rest of the data you transmit is transmitted without encryption if you do not use either VPN or Tor. The program encrypts only DNS traffic.
DNS LEAK
The
DNS Leak Tests
DNS Leak Test is a free tool for the internet allowing end users to test their DNS activity to see if their VPN or Proxy service is leaking DNS requests, effectively unmasking end user's privacy and security.
dnsleak.com
site allows you to identify a DNS "leak". Just go to this site. By clicking the Check for DNS leaks now button, you will receive a list of DNS servers through which your queries can pass. Therefore, you will see exactly who can find out which sites you visit.

INSTALLATION AND USE DNSCRYPT
The easiest way to secure your DNS connection is to use DNSCrypt.
First of all, download DNSCrypt itself from GitHub. To download the program from GitHub, click the Download ZIP button. The archive with the DNSCrypt sources will be downloaded. The already compiled version is in the archive's DNSCrypt directory. Unpack the files. Basically, you only need one file - dnscrypt-proxy.exe. It is located in the same directory. Everything else (sources) can be deleted.
But that's not all. If you've already googled it, then you've seen screenshots of DNSCrypt. By running dnscrypt-proxy.exe, you realized that something was wrong. The program was launched in a command prompt window. That's right, you downloaded the proxy itself, and now you still need to download a shell for it. There is another project on GitHub - the wrapper we need (https://github.com/Noxwizard/dnscrypt-winclient).
Download the ZIP archive in the same way, unpack it somewhere. The binaries / Release / directory contains the dnscrypt-winclient.exe program. Copy this file to the directory containing the dnscrypt-proxy.exe file.
All that remains is to run dnscrypt-proxy.exe. In the window that appears, select the network adapters you want to protect and click the Start button. If everything is normal, then DNSCrypt is running will appear next to the Stop button (the Start button will turn into it).


CONCLUSION
The article turned out to be not very long, since the program itself is very easy to use. But it would be incomplete if I didn’t mention VPN too. If you have read this article, you are interested in it, but you still do not use the services of a VPN provider to encrypt your data, then it's time to do it.
The VPN provider will provide you with a secure tunnel to transfer your data, and DNSCrypt will secure your DNS connections. Of course, the services of VPN providers are paid, but do you have to pay for security?
You can, of course, use Tor, but Tor is relatively slow, and this, whatever one may say, is not a VPN - all traffic cannot be "torified". Either way (whichever option you choose) your DNS connections are now secure. It remains only to decide on a traffic encryption tool (if you have not done it yet).
And in order to save money and not pay such a huge amount of money that VPN providers now take, you can order a VPN for 50% of the cost from @levynson. He has about 10 different VPNs available, but personally, I recommend taking only NordVPN. I hope that this information was useful to you, so I will be grateful if you share the link and this article with your friends and make a repost.







