Premiums
TRUSTED VENDOR
- Joined
- Dec 5, 2020
- Messages
- 3,203
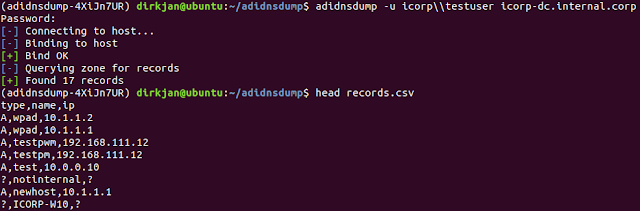
By default any user in Active Directory can enumerate all DNS records in the Domain or Forest DNS zones, similar to a zone transfer. This tool enablesenumeration and exporting of all DNS records in the zone for recon purposes of internal networks.
For more info, read the associated blog post.
Install and usage
You can either install the tool via pip with pip install adidnsdump or install it from git to have the latest version:
or
Code:
git clone https://github.com/dirkjanm/adidnsdump
cd adidnsdump
pip install
Code:
pip install git+https://github.com/dirkjanm/adidnsdump#egg=adidnsdump
GitHub - dirkjanm/adidnsdump: Active Directory Integrated DNS dumping by any authenticated user
Active Directory Integrated DNS dumping by any authenticated user - GitHub - dirkjanm/adidnsdump: Active Directory Integrated DNS dumping by any authenticated user
The tool requires impacket and dnspython to function. While the tool works with both Python 2 and 3, Python 3 support requires you to install impacket from GitHub.
Installation adds the adidnsdump command to your PATH. For help, try adidnsdump -h. The tool can be used both directly from the network and via an implant using proxychains. If using proxychains, make sure to specify the --dns-tcp option.





















